This article is more than 1 year old
The Pirate Party is the shape of things to come
The Angry Brigade are real winners from the Mandybill
The politics of spite
I think there are two ingredients to the Pirates' success, and they have little in common.
For any politics watcher, the Manifesto really is a completely fascinating bundle of contradictions. There's little attempt to disguise its motivation as a Single Issue party, as readers pointed out in comments here - but even there it falls over itself.
For a party of Pirates (yarrr!), you'd expect a minimal manifesto in the great tradition of the crypto anarchists. But in reality, it's surprisingly authoritarian: the Pirates' solution to every grievance is a new law or regulation. This is not the recipe for a Temporary Autonomous Zone.
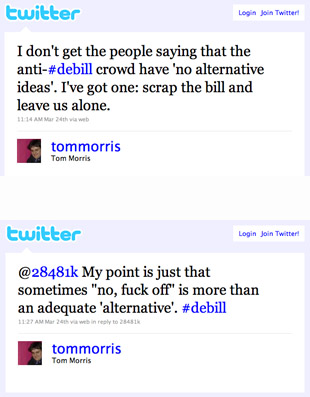
Even the universally hated National Identity Register would be kept on, apparently, but with extra conditions attached to it. Quite a few of you think that's bonkers. I agree, there's no other description.

Heroically, there's no attempt to soften the pill for creators. They're stuffed. All copyright expires after ten years (five years if you're not careful, and apply to re-register it) - so anybody can put out IBM's DB2, Microsoft's Windows, Martin Amis' books or the back catalogue of Michael Jackson (compositions and recordings) and not pay the author - pocketing all the proceeds for the "Pirate" version. You have to be extremely limited in your thinking not to see bad consequences from this, but for the Pirates the "benefit" of destroying these businesses outweighs any disadvantages. The Pirates are offering a politics of spite and selfishness.
With a few people, this strikes a chord. We'll call this the "nasty" brigade - being seen with these chaps does not improve your prospects of a date. But they're outnumbered by a larger group.
For far more people, the Pirates offer a simple gesture against the political elites. Most wish no ill towards creators, and couldn't justify them as collateral damage, as the Party does. But a vote (especially an electronic vote) for the Pirates is a snub to a system that people think has failed them.
So the Pirates' hour may have come. They've made a consumer issue into a civil rights issue, and all because of a lack of action from the music industry to exploit the technology available to it. That's what's resulted in a Bill that nobody really likes. Yes, there's a poetic justice (as my companion at the demo pointed out) to suspending somebody who uses the internet too much, and whose inflated sense of entitlement ("rights") means trampling over other people. It's cheaper to let them cool off at dial-up speed, than fuelling the quack medical profession and booking them into an "internet addiction" clinic. That's missing the point.
Except... lobbyists love a political vacuum
As I said earlier, file sharing is a real joy - it should be legal, not criminal. We ought to have competing file sharing services available to us, all innovating their file-sharey goodness. Unlike the Pirates, however, I just don't expect to get this pleasure for nothing. Many parts of the music business recognised the thrill offered by the original Napster a decade ago, and set about trying to convince rightsholders that they'd profit from it. So the argument is really about how to legalise it.
In other words, to get to the "sharing culture" they advocate, no group has to lose out, nobody need get poorer, and certainly, nobody has to have their rights taken away. To argue otherwise is pure, childish spite.
Onwards to a Pirate Future
Today the Parliamentary Pirate candidates say they're skint, and their ambition is merely to avoid losing their deposits. But that may soon change. Google lurks in the background, and its business strategy aligns perfectly with the destruction of online copyright. While the Pirates say they're not in hock to lobbyists, I expect that to change too. Google is too clever to fund them directly, but it may wish to launder some money via foundations or quasi-academic quangos.
Where there's a will, there's a way. ®
