This article is more than 1 year old
Tablet maker threatens, then robs Apple
The non-iPad iPad clone
The publicity whores at China's Shenzhen Great Loong Brother tablet-PC maker are at it again.
First, they raised a worldwild rumpus by floating the prospect of a lawsuit accusing Apple of stealing the design of their tubby P88 slate for the iPad. Now they've blatantly ripped off the look and feel of Mac OS X, pasted it onto Windows, and installed it on their aforementioned touchscreen tablet.
From the Chinese-centric gadget blog Giz-China comes word - and photos - of the oh-so-subtle "upgrade" to the P88.

Logo? Check. Dock? Check. Menu bar items? Check. Icons? Oops, wrong side...
Back when we first reported SGLB's threatened lawsuit, we ridiculed the company's president Wu Xiaolong for saying that the P88 and the iPad were "identical". That must have stung him, as he apparently went immediately to work making the device even more closely resemble a Cupertinian creation.
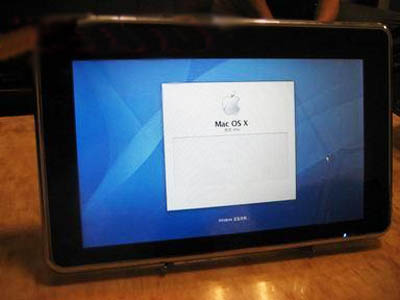
"What shall we call our rip-off of Mac OS X? Hmm... How about 'Mac OS X'?"
Unfortunately, Wu and his minions chose the wrong Apple device, ensuring that the P88 resembles a Mac - not an iPad.
But we've got to hand it to the Wu-ster. He has succeeded in getting another round of free publicity for his company.
Doh! We're such suckers. ®
