This article is more than 1 year old
Netgear ReadyNas NVX Pioneer Edition
Nifty Nas box
Review Reviewing the RNDX400E was difficult from start to finish, not least because we were sent the RNDX4210 instead first. It’s an easy mistake to make though, since both the RNDX400 and RNDX4000 (notice the extra zero) series share pretty much identical hardware.

Netgear's driveless ReadyNas NVX Pioneer Edition RNDX400E
The former (reviewed here) is Netgear’s new ‘Pioneer Edition’ Nas, which is essentially the same as the 4000 series but without hard drives and without Windows Active Directory, snapshot, iSCSI, NIC teaming/failover, SNMP and secure rsync features. Removing all those features make it inappropriate for many business environments, but there are still plenty of areas where the RNDX400E is extremely competent.
Once we had the right Nas in our hands, we were presented with a “corrupt root” message and no access to its configuration pages. Our first check was to see whether the Ram was dislodged, which can happen in transit. This is an easy check as Netgear exposes the Ram just behind the top panel. However, the Ram was fine and it turned out that pre-formatted hard drives were the culprit.
Whenever formatted drives are used you have to press a sequence of buttons on the Nas (reset, power, backup, backup, reset) to wipe them. It’s sensible for novices to understand their disks will be wiped when inserted into a Nas but it’s a pain that it can’t be done in software like on most other models. If you want to change the Raid type you’ll have to go through this button pressing mania too, combined with a bit of software called RAIDar, available for Windows, Mac and Linux.
Installing hard drives is a breeze, thanks to its four hot-swappable bays with latch handles. Other hardware features include three USB ports, two gigabit Lan ports and a dual line LCD. The power brick is fitted internally, reducing clutter, while the overall build quality is high.
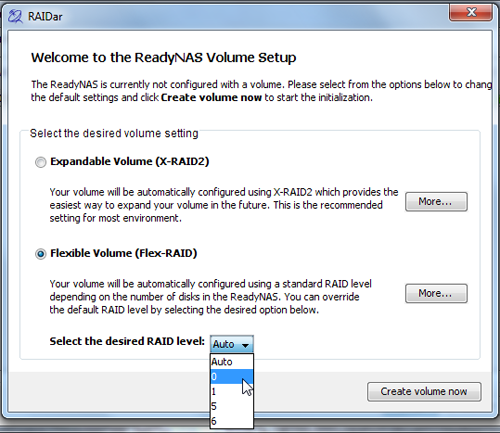
Numerous button presses, plus software tweaks are needed to change the Raid type
A fixed handle on the back of the Nas is, at first glance, one of the nicest design touches; it can be difficult to move Nas boxes about – even though they are small – because they can weigh quite a few kilos, so a handle makes perfect sense. However, we came to distrust it because the Nas swings downwards as you lift the handle and this motion twice caused the fan grill to take chunks of skin out from the knuckles.
