This article is more than 1 year old
Google doppelgänger casts riddle over interwebs
Why is Google routing the world through 'Googol'?
Updated Update: This story has been updated with comments from Google open source guru Chris DiBona and it has been revised accordingly.
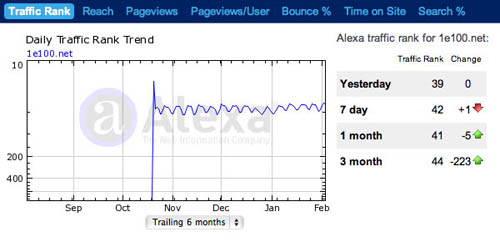
Sometime in the middle of October, Google silently launched a new net domain - a barely-disguised doppelgänger to the familiar google.com - and according to the latest stats from the site watchers at Alexa, this mystery domain is now visited by nearly three per cent of all net users, making it the 44th most visited domain on the interwebs.
In other words, it's bigger than AOL, Apple.com, or the BBC.
Over the past few months, those keeping a close eye on their PC's net traffic have noticed seemingly random connections to this mystery domain. In some cases, the connections arise even before an application is launched, and since the domain name appears - at first glance - to be little more than a hodgepodge of characters, some netizens have blocked it, under the assumption it serves up malware.
But on closer inspection, the domain is obviously Google's, chosen with a mathematician's wink at the search giant's famously misspelled name. This mystery domain is 1e100.net. "1e100" would be scientific notation for 10 100, a one followed by 100 zeros, also known as a googol.
As pointed out by Sebastian Stadil, founder of the Silicon Valley Cloud Computing Group, 1e100.net translates to "Google Network" - the ever-growing Google private infrastructure that spans nearly forty custom-built data centers worldwide. According to a recent company presentation, Google intends to expand this private interweb to between one million and 10 million servers, spanning “100s to 1000s” of global locations.
Who Is records show that Google registered 1e100.net on September 24, and according to data from Alexa, traffic began hitting the domain around the middle of October.
'Googol' goes live
Asked for comment, Google merely said the domain is used to "identify the servers on our network," and it hinted that such identification involves reverse DNS lookup - the process of determining which domain name is associated with a particular IP address. Reverse DNS is often used by anti-spam services to verify email senders, but it's also used a general means of ensuring a network is working as it should be working.
"That was my first guess," Silicon Valley network architect Richard Bennett, tells The Reg, when asked about Google's brief comments on the new domain. "But it doesn't explain why Alexa sees it. I don't know what Reverse DNS has to do with it." Alexa - now owned by Amazon - tracks net traffic via toolbars installed on netizen browsers.
In a post to Slashdot, Google's Chris DiBona says that 1e100.net was launched to provide a single domain to identify servers across the Google network rather than doing so on separate domains. "Starting in October 2009, we started using a single domain name to identify our servers across all Google products, rather than use different product domains such as youtube.com, blogger.com, and google.com," he writes.
"We did this for two reasons: first, to keep things simpler, and second, to proactively improve security by protecting against potential threats such as cross-site scripting attacks. Most typical Internet users will never see 1e100.net, but we picked we picked a Googley name for it just in case."
According to various web posters and Register readers, any number of Google services interface with the domain - from Google Chrome's "safe browsing" feature to YouTube to the company's main search engine. Reg reader David Gray, a UK-based security consultant, sees connections to the domain that apparently involve Google Chat, Adsense, Google Analytics, Gmail, and Google Earth. "Essentially, it seemed to be all Google traffic," he says.
Using a Wireshark network protocol analyzer on a machine at our San Francisco offices, The Reg was unable to identify such connections, but Gray shared a network capture file where the connections are myriad.
Another net poster sees such traffic after boot-up but before launching any local applications. Among his installed services, this poster sees Google's updater software, used to provide software updates for various local Google applications, but he says the traffic occurs when the updater is not running.
Alexa stats also indicate this 1e100 traffic spreads to machines across the globe.
