This article is more than 1 year old
Elgato DTT Deluxe
World's smallest USB TV tuner
The Deluxe's antenna slots into a wee MCX (Mini Coax) port at the opposite end to the USB connector. Elgato bundles a standard mini antenna with a magnetic base and separate suction cup. It pivots at the base to allow you to maximise reception, as does the separate, telescopic aerial it provides. The latter is handy if you don't want wires spoiling the lines of your laptop and is more travel friendly too. Finally, if you need a feed from a full-size antenna, there's a mcx-to-coax adaptor in the box as well.

Elgato bundles two types of mini antenna, including a telescopic one
You'll certainly want to use the adaptor if you plan to plug the Deluxe into a desktop machine or media centre near to your TV. We found the reception surprisingly good with a mini antenna - certainly better than it has been with TV tuners we've tried in the past in the same London locations and with the same antenna types.
That said, it's by no means a match for a proper feed - thanks to Freeview's broadcast strength rather than any failing on the tuner's part. Our initial, extensive tune-up in Register Hardware's sixth-floor, central London HQ still missed a number of channels and couldn't get sufficient signal for some of the others.

EyeTV 3 playback...
Adjusting the mini antenna helps - you'll appreciate the pivot when you're moving at around in search of a signal - but unless you're in a very good locale, you'll need a proper aerial feed if you want the full selection of channels.
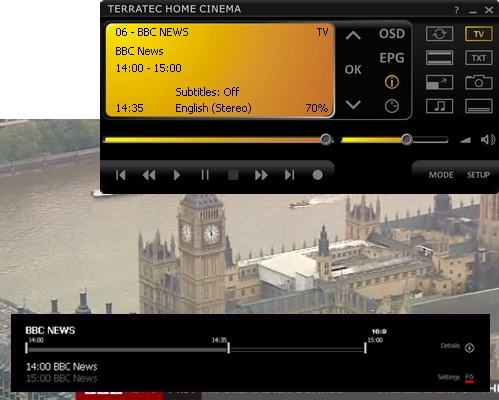
...and from Terratec Home Cinema
On a Mac, the Deluxe works with Elgato's EyeTV 3 software, which provides full DVR functionality, augmenting the over-the-air programme guide data with a year's free access to the TVTV online EPG. You can create lists of favourite channels; record, pause and rewind live broacasts; schedule recordings, top and tail them then convert them into formats suitable for playback on iPods, iPhones and Apple TVs.
