This article is more than 1 year old
Hands on with Acer's 3D laptop
Polarising specs at the ready...
First Look Acer will enter the record books today by releasing the world’s first 3D-capable laptop. So Register Hardware caught-up with the firm behind the technology – Dynamic Digital Depth – to discover how 3D content will look on Acer’s machine.
The 15.6in Acer Aspire 5738DZG 3D laptop has a screen that is coated with a thin 3D film. You wear polarising glasses rather than active shutter or red and green anaglyph glasses.
Can't see the video? Download Flash Player from Adobe.com
DDD’s TriDef software, which can be used with any GPU, facilitates playback of both 2D and 3D content, company President Chris Yewdall told Register Hardware.
Our initial response to the on-screen 3D display was good and - despite it only being capable of a 720p resolution – the content was clear, crisp and vibrant.
The depth of the 3D image displayed depends heavily on the screen’s tilt angle. Angle the screen too far forward or too far back and you’ll probably only see a blurred 2D image – as you do when you take the glasses off altogether.
While the laptop is supplied with a stylish and light pair of polarising glasses, Yewdall claimed that opticians aren't too far away from offering to make up prescription 3D glasses. In the short-term, though, DDD can also supply a pair of clip-on polarising specs.
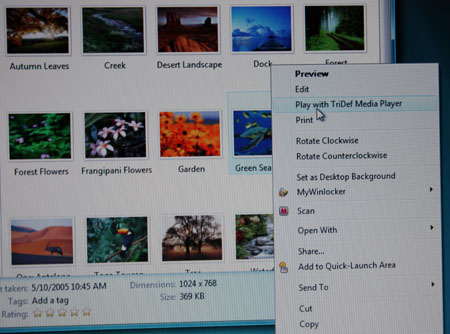
Converting 2D into 3D is as simple as right click with TriDef
Acer’s 5738DG won’t display everything in 3D, so you can forget browsing through Windows 7’s icons in 3D or jazzing up Excel with 3D spreadsheets. TriDef is largely limited to media content.
TriDef enables almost any 2D content to be transformed into 3D, Yewdall explained, as he took us through a slideshow of 2D photos converted into 3D. He also showed us a selection of movies and games that TriDef converted into 3D.
For the user, this conversion process is as simple as right-clicking on say, a JPEG, and selecting “Play with TriDef Media Player”.
The difference in 3D quality between a film and JPEG or videogame was negligible, in our opinion.
