This article is more than 1 year old
Remote IT support 'is harder'
Local support to local people?
Poll Results Perish the thought that we at Freeform Towers should try to over-simplify things, but from the whopping 465 of you who responded to this week's Reg survey, it is clear that there is more to 'remote support' than meets the eye.
In analysing the responses we agreed with comments from Reg regular Trevor Pott, that "a true 'remote user' is anyone who has to operate primarily outside the corporate firewall."
Indeed, the most straightforward way to consider remote users was to identify those who were not central office-based. On this basis, according to respondents the majority of users are office-based in only a third of organisations researched (figure 1).
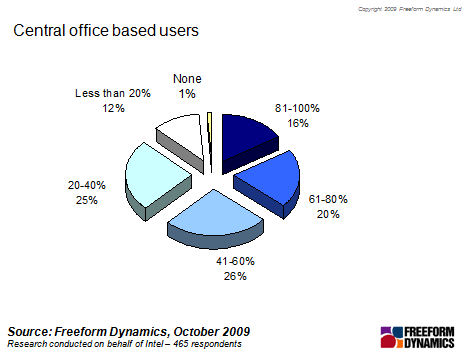
Figure 1
In this poll we were primarily interested in finding out how remote support experiences vary between local remote users. Mucho gravitas/lucky you to the six per cent who told us that in fact providing IT support to remote users is easier, but for the majority it ranks as 'a bit harder' or 'much harder'. OK, perhaps we could have anticipated that, but what’s interesting is not just the absolute measure, but the numbers of you out there making the same comments about how and where issues arise (figure 2).
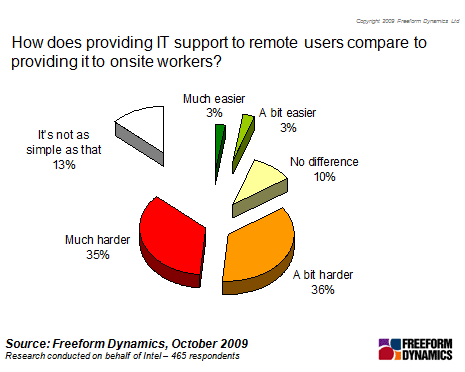
Figure 2
So what are the issues you face? We get some insight into the specifics (figure 3) when we consider the obvious status of a remote worker. Despite the existence of tools designed to help in these situations, we find the simple – yet insurmountable – truth that you can’t get up and go visit a user at their desk side does have a pretty big impact on providing support to them.
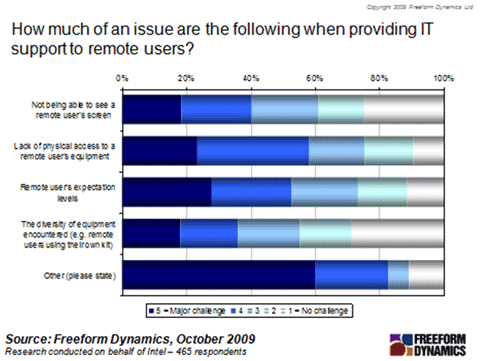
Figure 3
One element of this that is interesting was how highly you ranked ‘expectation levels of remote users’ as being a factor contributing to making things more difficult.
On the one hand, a remote user’s expectations may be simply the same, or lower than those of an onsite worker for the simple reason that they may consider the physical separation to count for something (which it does) and afford IT support some slack. On the other hand, if they are fairly used to remote working and have been given access to the corporate applications they need and have the rest of the world at their fingertips via the Internet, why should IT support be an issue? Regardless, those at the short end – doing the supporting – acknowledge this factor as making their jobs harder.
But the size of the ‘other’ bar is hard to ignore, which goes some way to suggest the complexities in this area – and this is where the freeform responses come into their own. Based on your responses we grouped similar issues into the following categories:
- ‘User availability’: e.g., keeping to agreed times, working ‘strange’ hours
- ‘Level of IT literacy’: most of these were not really printable :)
- ‘Communication’: users not being able to articulate their problems
- ‘Attitude of user’: reticence to follow instructions, honesty about which Internet sites visited
- ‘Blurring of boundaries’: between business and home computing
- ‘Connection’: ‘can you fix my internet connection?’ / ‘dodgy home networks’
Some of these are extensions of those you would expect to see in any user environment, but the physical separation compounds the problem. A good example is where problems occur due to the difficulties of communicating with users of relatively low technical literacy. Needless to say, if you can get around that issue by visiting their desk, great. But with a remote user you must plough on, despite the encounter being frustrating for both user and IT practitioner. The issue of availability can also add to the challenge – and to be fair, it is not something that can be solved by the service desk alone.
It would be easy at this stage to descend into motherhood and bring up the topic of regular end-user training. But we know from other studies that there are certain points at which a little bit of smart thinking can save a lot of effort later – for example, giving users a brief checklist of common issues and how to resolve them, do’s and don’ts and so on. In some cases we understand it may be pertinent to require that a specific piece of training or knowledge be assimilated before ‘remote IT rights’ are granted, but often this can be done using computer-based training, i.e. without any overhead on support.
We saved the best comment until last. We’d love to know how common this particular gem is, submitted by a Reg reader: “Kids murdering each other in the users background make it hard to hear”.
Given the frustration that some of you expressed regarding providing support to users with low levels of IT literacy, perhaps one way round this would be to ask their kids to stop trying to kill each other and for one of them to come and speak on the phone.
