This article is more than 1 year old
Iomega StorCenter ix4-200d
Eco-friendly four-bay Nas?
Both have four 500GB hard drives – Seagate Barracuda LP in the ix4-200d’s case – USB ports, two Ethernet ports, an LCD screen and so on. The biggest physical difference is that the Terastation’s hard drives are easily removed from a front door, while the ix4-200d’s are more permanently stored away. You can still remove the hard drives, but first you just need to undo a couple of screws and three sided of the case.

The settings page reveals most of standard Nas features you’d expect
Configuration is done solely from a web interface, with the bundled CD providing a manual, device finding software and EMC Retrospect Express HD for backing up files. The ix4-200d’s web interface has a crispness to it that the Ajax interfaces from Qnap and Synology lack.
Features are divided into sensible categories, with separate pages for the web file browser, settings and user control. All the standards you’d expect from a high end Nas are supported like CIFS, SMB, NFS, AFP (including native Apple Time Machine support), FTP, Windows Active Directory so Windows, Linux and Apple users should all be happy.
At first glance, the ix4-200d provides an excellent DynamicDNS solution for remote access. From the ix4-200d’s web interface you simply choose a name for Nas and pick between iomegalink.com or myiomega.com domain names and you’re away.
However, after the first year you’ll be charged $9.95 annually for the service and you can’t use alternative, namely free, DNS services either, unless you configure your router to do the job of remote access instead.
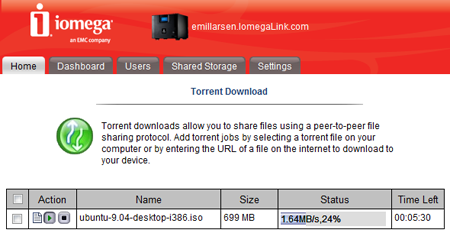
BitTorrent port selection is restricted, although our speeds were fine
DLNA compatibility hints the ix4-200d has a few consumer features, with 1080p PS3 and Xbox360 streaming no problem. BitTorrent downloading is also handled through the browser. However, we discovered you could only choose a port between 6881 and 6999, ports that used to be and, most likely still are, throttled by ISPs.
