This article is more than 1 year old
Crucial CT256M225 256GB SSD
The best value solid-state drive yet?
If you take the two sets of synthetic benchmarks together, the Patriot and Crucial SSDs have the same level of performance. However, the variations in write speeds are noteworthy.
ATTO Test Results
Crucial CT256M225
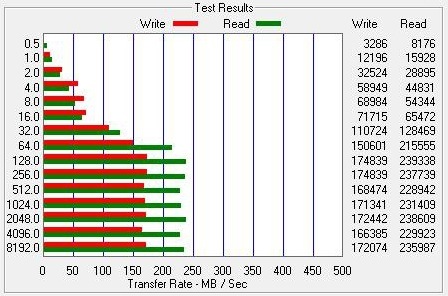
In our real-world file transfer tests, we copy folders that contain 2GB of files. We started, as usual, by transferring files within the drive and saw that the time taken for the test was pretty much identical for the Patriot and the Crucial. When you consider that the two drives are very similar, apart from their capacity, this is what we expected to see.
Transferring files from one drive to another revealed a more complex situation. When we used a second-generation Intel X25-M drive as the other half of the pair we saw that the Crucial SSD was marginally slower than the Patriot when reading files from the Intel drive. That’s marginal as in a fraction of a second out of 16 seconds, which equates to around six per cent. By contrast, when we read files from the test drive and wrote them to the Intel X25-M, we found that the Crucial drive was significantly faster than the Patriot to the tune of five seconds with big movie files and ten seconds with smaller music files. That’s a huge margin of 25 per cent in favour of the Crucial.
As a final test we switched the paired SSD from the 160GB X25-M to the older, first-gen 80GB X25-M and this threw up some more oddities.
ATTO Test Results
Intel X-25M 2G
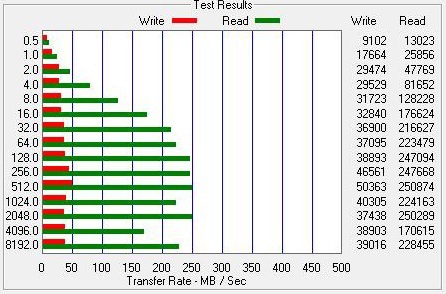
When we transferred files between the original X25-M and the Patriot all of the transfer speeds slowed by a significant amount. In the case of the Crucial drive, the read times were unaffected but the write times took a similar clobbering to those that we saw on the Patriot.
