This article is more than 1 year old
Treemometers: A new scientific scandal
If a peer review fails in the woods...
Hokey hockey sticks
Mann too used dendrochronology to chill temperatures, and rebuffed attempts to publish his measurement data. Initially he said he had forgotten where he put it, then declined to disclosed it. (Some of Mann's data was eventually discovered, by accident, on his ftp server in a directory entitled 'BACKTO_1400-CENSORED'.)
Tree data was secondary in importance to Mann's statistical technique, which would produce a dramatic modern upturn in temperatures - which became nicknamed the "Hockey Stick" - even using red noise.
Similarly, all the papers that used the Yamal data have the same point to make. All suggest recent dramatic warming. Having scored a global hit with a combination of flawed statistics and dubious dendroclimatology, the acts repeated the formula.
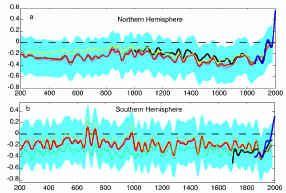
"Late 20th century warmth is unprecedented for at least roughly the past two millennia for the Northern Hemisphere," wrote the two authors of Global Surface Temperatures over the Past Two Millennia published in Geophysical Research Letters in 2003 - Mann, and Phil Jones of CRU.
For example, Briffa's 2008 paper concludes that: "The extent of recent widespread warming across northwest Eurasia, with respect to 100- to 200-year trends, is unprecedented in the last 2000 years."
The same authors in 2004:
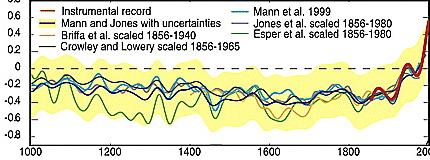
It continues to this day. A study purporting to show the Arctic was warmer now than for 2,000 years received front-page attention last month. Led by Northern Arizona University professor Darrell S Kaufman, and including dendro veteran Mann, this too relied heavily on Yamal, and produced the signature shape.
Now here's Yamal.
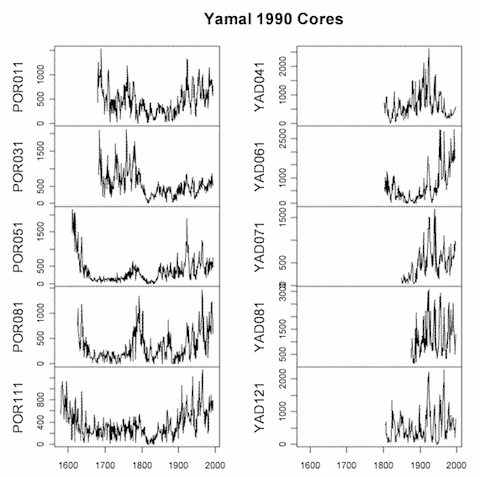
And when Yamal is plotted against the wider range of cores, the implications of the choice is striking:
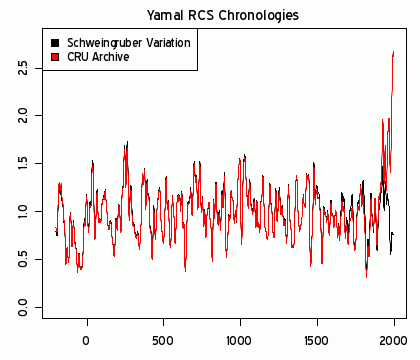
A comparison of Yamal RCS chronologies. red - as archived with 12 picked cores; black - including Schweingruber's Khadyta River, Yamal (russ035w) archive and excluding 12 picked cores. Both smoothed with 21-year gaussian smooth. y-axis is in dimensionless chronology units centered on 1 (as are subsequent graphs (but represent age-adjusted ring width).
"The majority of these trees (like the Graybill bristlecones) have a prolonged growth pulse (for whatever reason) starting in the 19th century," wrote Canadian mathematician Steve McIntyre on his blog on Sunday. "When a one-size fits all age profile is applied to these particular tries, the relatively vigorous growth becomes monster growth - 8 sigma anomalies in some of them."
McIntyre's determination to reproduce the reconstructions has resulted in the Yamal data finally coming to light.
All the papers come from a small but closely knit of scientists who mutually support each other's work. All use Yamal data. And without the Yamal data, the temperature record shows a very different shape.
