This article is more than 1 year old
Nokia intros X series
New name, look for XpressMusic line
Nokia didn't just unveil the N97 Mini this week, it also introduced its first X-series phones, the successors to its XpressMusic line.
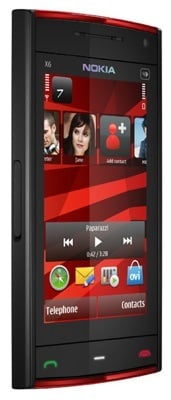
Nokia's X6: a new look for Comes With Music phones
The top-of-line model is the X6 and sports a 3.2in, 16:9 touchscreen and 32GB of storage capacity - there's no memory card slot - all in a 14mm-thick casing. Round the back is a 5Mp camera with Carl Zeiss optics and a twin-LED flash. The handset has Assisted GPS too and a TV port.

Carl Zeiss lens work
For connectivity, it has HSDPA 3G, Wi-Fi and Bluetooth 2.0.
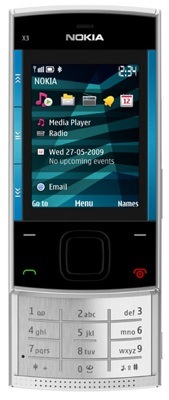
X3: no touchscreen here, just a keypad
The significantly cheaper X3 makes do with a 3.2Mp camera and a 2.2in, 240 x 320 display. It's only a quad-band GSM/GPRS/Edge device too. But it does have an FM radio and a slide-out keypad. It has Bluetooth 2.1 and can take Micro SD cards.

Not as svelte as its sibling
Both the X6 and X3 will go on sale in Q4, Nokia said. Pre-subsidy and pre-tax prices are €450 (£322/$663) and €115 (£82/$169), respectively. ®
