This article is more than 1 year old
Getting down and dirty with desktop virtualization
Drilling down on real world practicalities
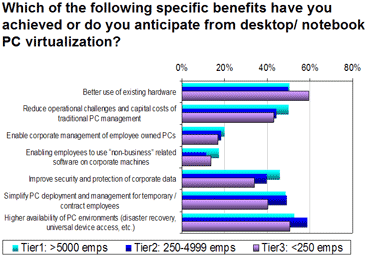
Reader Workshop As discussed earlier this week there is growing interest in desktop virtualization, despite many IT professionals having limited detailed knowledge of the technologies in this area. The chart below, for example, taken from a Reg Tech Panel survey, indicates a good awareness of the potential benefits across all sizes of organisation.
The fact that no one benefit stands out as the leading reason for considering desktop virtualization offerings in many ways reflects the very wide range of challenges that beset those charged with supporting desktops. The truth is that the cost of supporting the desktop remains a black hole in most IT budgets
Meanwhile, the survey indicated that higher level factors such as improving service reliability and providing better service levels to users, along with a more rapid response to changing business requirements, were almost neck and neck with cost reduction. People who support desktops have typically struggled with these matters for years.
The potential benefits of desktop virtualization are therefore extensive, but it must be remembered that deployment of any virtual desktop infrastructure (VDI) solution has impacts beyond the desktop kit itself and how it is used.
Depending on the approach, the server and network infrastructure could be put under considerable additional stress. This is a factor to bear in mind when evaluating specific technologies such as bladed solutions to host virtual desktops on a 'one to one' model, versus more of a shared server type of infrastructure. Conceivably, the business may need to use more than one approach to cater for discrete service requirements in different areas.
The storage impact in the data centre where the central repository of images is kept is another area to be considered. If an organisation decides, consciously or not, to simply provide every user with their own image, the volume of additional data that needs to be stored and managed will be significant, and the costs involved need to be factored into the business case.
Fortunately, given that a very large proportion of the data contained in any particular desktop is likely to be identical with most others, there is clearly an opportunity to de-duplicate. Ideally, for example, just a single image of the mainstream desktop would exist, then information on the differences or additions required by each user would be maintained by exception.
As a by product of such an approach, it is more straightforward to patch/maintain a single (or at least small number of) virtual desktop images than dealing with tens, hundreds or thousands separately. The potential use of streamed applications is another area that may merit consideration. The desktop itself is as simple and standard as possible and each user simply pulls down the virtualised application images they need on top of this as when they require them.
Uncultured
One challenge may surpass all of the technical considerations we have discussed.
This is the small matter of changing the culture and perception that users have created around the machine they have been allocated as being "their PC" rather than their employer’s. In practical terms, this is about the user having become accustomed to customising the machine in any way they wish, irrespective business requirements. Irritatingly for those in tech support, the only time when this possessive behaviour typically abates, albeit for a limited time, is when there is a problem when the machine that needs fixing.
If that's the way it is in your organisation, we would be interested in your views and any tips you might have for driving cultural change. And on the broader topic of desktop virtualization adoption in general, let us know whether you believe the kind of benefits highlighted above are relevant and, indeed, real.
Conversely, what are the kind of things that can impair a move in the virtual desktop direction, and what are the ways to work around them? It would be particularly interesting to hear from anyone that has undertaken a desktop virtualization trial, proof-of-concept, or even a full roll-out.
Join the debate by adding your comments below.