This article is more than 1 year old
Collar the lot of us! The biometric delusion
Optimism beats evidence in the drive to fingerprint the world
Suppose that there were 60 million UK ID cardholders. To prove that each person is represented by a unique electronic identity on the population register, each biometric would have to be compared with all the rest. That would involve making 1.8 x 1015 comparisons.
Suppose further that the false match rate for biometrics based on either facial geometry or fingerprints was one in a million (1 x 10-6). It isn’t. It’s worse than that. But suppose that it was that good, then there would be 1.8 x 109 false matches for IPS to check.
It is not feasible for IPS to check 1.8 billion false matches. It is therefore not feasible for these biometrics to do their identification job.
Verification on the other hand, according to Tony Mansfield, is millions of times easier, and requires only that your facial geometry match the photograph recorded on your ID voucher (whether a passport or an ID card or a biometric visa) or that your fingerprints match the templates recorded on the voucher that you proffer to an immigration control officer, for example, or to a bank manager or to a GP, to underpin your transactions and interactions with them.
It may be millions of times easier, but can the biometrics chosen for the NIS achieve even the job of verification?*
Apparently not.
In 2004, the UK Passport Service (UKPS, now IPS) conducted a biometrics enrolment trial. 10,000 of us took part and a report of the trial was published in May 2005.
Under the heading Key Findings (para.1.2), sub-heading Verification Success Rates (para.1.2.1.4), the report says that 31 per cent of people could not have their identity verified using facial recognition technology – they were told that they did not match the photograph of them taken only five minutes before. And that was just the able-bodied participants – for the disabled, the false non-match rate was 52 per cent. And, using flat print fingerprinting technology, 19 per cent of the able-bodied participants could not have their identity verified, and neither could 20 per cent of the disabled**.
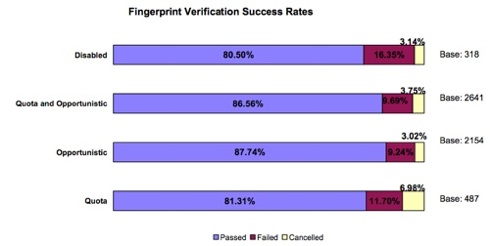
Fingerprint verification results from the 2004 trial
With some people, you can give them any amount of evidence, they will continue to believe that the Earth is flat.
Failure rates of 19 and 20, and 31 and 52 per cent clearly scupper IPS’s plans for the NIS. Millions of us would be unable to prove our right to work in the UK if that proof depended on biometrics, we would be unable to obtain non-emergency state healthcare and our children would be barred from state education.
* Verification is a source of some confusion among politicians and the media. If my flat print fingerprints match the templates stored on an ID voucher, then the biometrics have successfully completed their verification job. But was the ID voucher issued by IPS? And even if it was, have I tampered with it since then and inserted my biometrics? The technology needed to answer those further questions and help to make the NIS secure is PKI – the public key infrastructure – and not biometrics. Even David Blunkett gets the two confused, which is surprising considering that he had a job with a PKI company, Entrust, Inc.
** Traditional rolled prints are trusted worldwide and are admissible as evidence in court. But IPS propose to use the new technology of flat print fingerprinting (para.30.86), which is quick and clean, requires no expert in attendance, but appears to fail 19 or 20 per cent of the time and it is not admissible as evidence in court. To give these two different technologies the same name, “fingerprinting”, is literally a confidence trick. According to Professor Daugman, the key to a biometric is the amount of randomness and complexity that it contains. 'Face recognition is inherently unreliable because there isn't nearly enough randomness in the appearance of different faces. Fingerprints are vastly better biometrics than faces,' he says, 'but better still are iris scans'". But note the problem discovered in the UKPS biometrics enrolment trial (para.1.2.1.3). 10 per cent of able-bodied participants were unable to register their iris scans in the first place. That figure rose to 39 per cent for the disabled.
