This article is more than 1 year old
Underground forum r00t-y0u.org gets pwned
S'kiddie defacement or law enforcement sting?
A notice on underground cybercrime forum r00t-y0u.org on Thursday suggested the site had become part of a law enforcement sting operation. However hacker hijinks and mischief making seem equally likely explanations for the incident, at the time of writing.
r00t-y0u.org's home page has been replaced by an jpg image notice stating that the previous cybercrime activity on the site has been logged and will be passed on to appropriate law enforcement agencies. It's unclear who posted the advisory, which was spotted by security researcher Mikko Hypponen of F-Secure, or even whether it is genuine.
No law enforcement agency is identified on the notice.
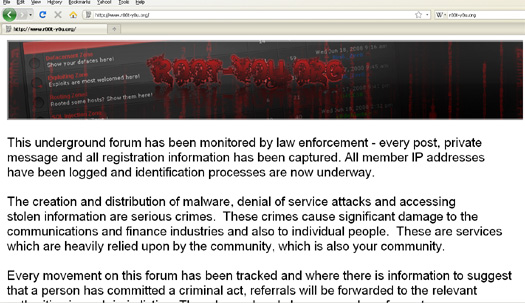
Roots you, sir.
Chris Boyd, a security researcher at Facetime, and long time nemesis of s'kiddies, cautions that several underground hacking forums were defaced recently and the r00t-y0u incident might be related. Bearing this important caveat in mind, the notice on r00t-y0u.org states.
This underground form has been monitored by law enforcement - every post, private message and all registration information has been captured. All member IP addressed and have been logged and identification processes are now underway.The creation and distribution of malware, denial of service attacks and accessing stolen information are serious crimes.
The notice goes on to suggest arrests will follow.
Every movement on this forum has been tracked and where there is information to suggest a person has committed a criminal act, referrals will be forwarded to the relevant authority in each jurisdiction. There have already been a number of arrests as a result of current investigations. This message should serve as a warning not to engage in criminal activity.
Law enforcement infiltration of underground forums is rare but not unprecedented. The DarkMarket carder forum was famously taken over in a months-long FBI sting last year. Around 56 people worldwide were arrested over their involvement their activities on DarkMarket, which posed as a forum for identity thieves, carders, and other cybercrooks.
Defacement of underground forums is a far more common incident. Motives might include a desire to discredit a rival forum, among other reasons. ®
