This article is more than 1 year old
Canadian telco uploads 8GB iPhone 3GS
Pre-release hint or keyboard slip-up?
Canadian electrical retailer Rogers has as near as darn it confirmed that an 8GB iPhone 3GS is on its way, briefly revealing the device in a handset comparison chart on its website.
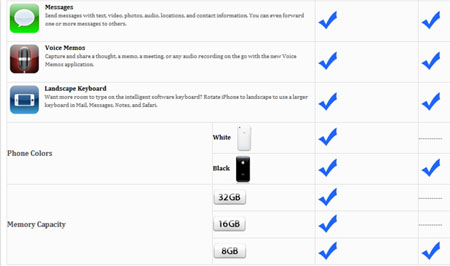
Rogers' comparison chart: iPhone 3GS features on the left and iPhone 3G features on the right
A section of Rogers’ website allowing buyers to compare and contrast the various features of the iPhone 3G and 3GS until very recently showed the option of an 8GB 3GS, although the low-capacity 3GS isn’t yet available to buy or order anywhere on the site itself.
We feel obliged to point out that because other areas of Rogers’ website only mention 16GB and 32GB 3GS models, the comparison chart’s 8GB 3GS reference may just be a typing error. Indeed, the tick by the 8GB 3GS shown in the picture above has now been removed.
However, it comes less than one week after details of a Rogers document appeared to outline the retailer’s plans to add an 8GB iPhone 3GS to its inventory.
The document also alleged that Rogers is planning to phase out the 8GB iPhone 3G, which is still available to buy through its website.
Apple hasn’t announced any plans to launch an 8GB iPhone 3GS. ®
