This article is more than 1 year old
Cutting the cord: future mobile broadband tech
How internet on the go is going to get much faster
In the UK, WiMax is only used for fixed connections, a space where it will probably continue to be deployed for a few years until the Intel dollars dry up - LTE has aspirations there to.
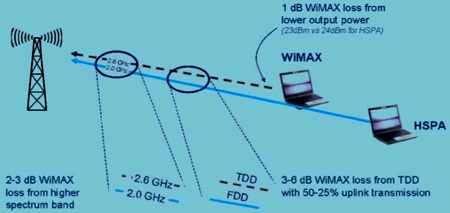
Range considerations: WiMax vs HSPA
Source: Ericsson
But nothing is going to happen until the middle of 2010 when Ofcom launches the mega-auction of Digital Dividend spectrum - between 400MHz and 800MHz - along with a chunk of 2.6GHz that should have been auctioned off last year, but couldn't because of T-Mobile and O2 legal actions that are only now being resolved. Once that spectrum is in private hands, we'll start to understand to what use those hands intend to put it, though deployments will probably wait until some time around 2012.
What isn't clear is if we'll see many phone handsets capable of switching between 2G, 3G and 4G technologies. In the US, WiMax is being pitched as a wireless data network for laptop computers, rather than a voice service, and it's probably computers that will drive LTE adoption rather than handsets, at least initially.
Few regions have sufficient 3G coverage to even contemplate switching off 2G services, though with greater spectrum liberalisation allowing 3G deployments at 900MHz and lower, that should change. So the only question is if network operators will expand their 3G networks the fill the cities with LTE, or simply deploy LTE everywhere and quietly forget that 3G ever existed.

Modem makers are already gearing up for LTE
Image courtesy Mobil.se
WiMax will probably still be lingering around then: Intel has spent millions promoting the standard and won't walk away easily. But LTE is effectively unstoppable now and the standard has been formally endorsed by so many mobile operators as to guarantee its eventual domination of, and possible monopoly on, wireless communications in the long term. ®
