This article is more than 1 year old
Feds: Hospital hacker's 'massive' DDoS averted
Arrest foils 'Devil's Day' scheme
GhostExodus outed
In some respects, McGraw's hacking regimen bordered on the paranoid. He kept a webcam over the outside door to his one-bedroom apartment so he'd know in advance when someone was calling on him. But otherwise, court documents portray someone who was sloppy in covering his tracks. The picture on a fake FBI credential he showed in one video matched the photo on his driver's license. Another video in which GhostExodus showed off Wireshark and other hacking tools revealed an IRC session that revealed an IP address issued by swbell.net.
His need for attention led him to volunteer a wealth of information about himself. A profile here made in March lists his age as 24 and shows the face of a white male that is identical to the one belonging to the individual McGrew says he observed in the hospital videos. (Those clips have since been taken down).
Combining the IP address with a Craigslist posting and GhostExodus's YouTube videos, McGrew soon deduced the miscreant probably was a night security guard at Carrell Clinic.
Besides breaching the security of the hospital, McGraw also posted evidence that he accessed a computer used by the aviation unit of the Dallas Police Department. Police officials confirmed that a machine assigned to that unit was known "to have been compromised by an unauthorized individual."
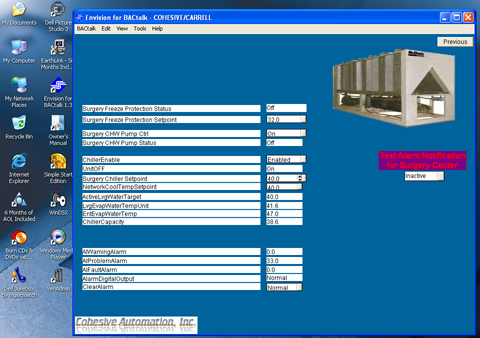
McGrew - who despite the name similarity has no relation to McGraw - first learned of the HVAC breach after someone from Electronik Tribulation Army sent him an unsolicited instant message on June 18 bragging of the exploit. The message pointed to screenshots that suggested it wasn't a hoax. With a specialty in SCADA, or supervisory control and data acquisition, McGrew quickly took notice. Three days later he tipped off the Texas Attorney General's office and the FBI.
"I can't just see that and let that go," he said. "I spent the entire weekend trying to find out as much about GhostExodus as possible."
Of particular concern was the sinking realization that someone had unauthorized access to the system that controls the air-conditioning systems that cool operating rooms and other critical areas of the Texas hospital, where temperatures regularly hit the triple digits.
"Elements of critical infrastructure, like HMIs for control systems in hospitals have such low security that even someone like this can get in," he said. "It really shows how dangerous even a low-skilled attacker can be." ®