This article is more than 1 year old
Shuttle XPC SX58H7
Monster CPU, miniature chassis
There are two parts to the cooling system. There's the ICE cooler that transfers heat from the CPU to a heat exchanger at the rear of the case where it is blown into the outside world by a 90mm case fan. The second part is the Oasis cooler, which uses heatpipes that loop around the CPU socket to link coolers on the northbridge, southbridge and power regulation hardware. The single ATA-133 connector and three ATA connectors are arranged at the front of the motherboard where the cables have an easy route.
PCMark 05 Results
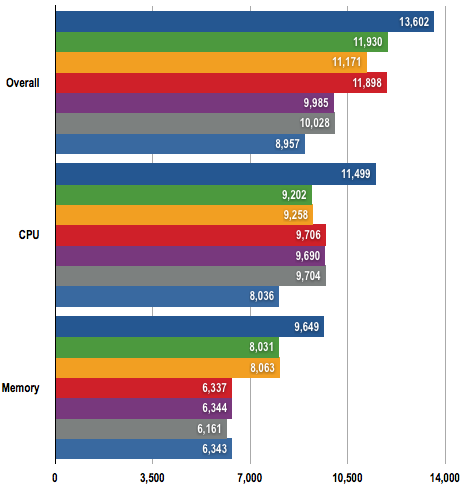
Longer bars are better

You need to supply a processor, memory, a hard drive, an optical drive, a graphics card and an operating system to turn the SX58H7 barebones into a finished PC. When you consider that the cheapest intel Core i7, the 920, costs £220, you know the build isn’t going to be cheap, but you may need to sit down when you learn that the Shuttle SX58H7 itself costs £529. This takes the cost of a fairly basic system north of £1000, and if you fancy proper gaming graphics the cost is likely to be higher than £1200.
