This article is more than 1 year old
Solwise 3.5G plus WLAN Mobile Server Router
DIY networks, wherever you go
As we say, all this is largely what you'd expect a well-featured router to provide, either up front or tucked away under an Advanced Settings tab. But it's surprising to find all this stuff on a travel router. Incidentally, it'll also operate as a plain wireless access point or as a wireless pick-up for one Ethernet-connected device - just flip a switch on the side to set the mode you want.
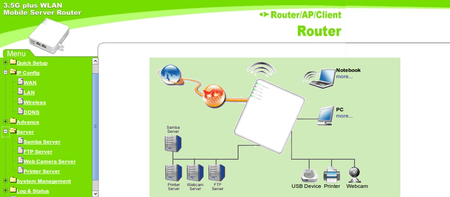
The web UI's basic but comprehensive
Could you use it as your main router at home? Possibly, but we found that its Wi-Fi signal wasn't as strong as the one in our own wireless router. It's hotel-room usable, we'd say, but it doesn't have the quite range of a regular router.
It seemed to operate more effectively with the unit set to Access Point mode, in which it simply acts as pipe connecting wireless and wired clients to a network's main router.
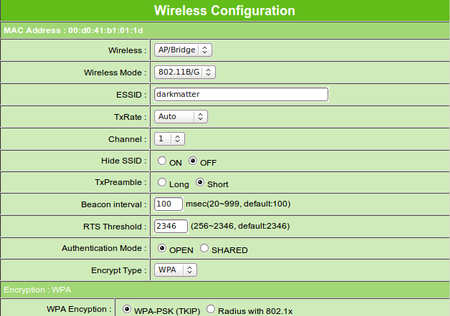
Create a WLAN or extend an existing one
HSDPA connectivity worked, but you should check with the Solwise website that the dongle you use is supported by the MSR, though every firmware update adds more to the list. Officially unsupported modems may work, but it's not guaranteed. Our Huawei E176 isn't listed, for example, but we could connect, and the MSR handed over to the modem when we yanked the cable connecting it to our broadband box. That said, it did have a habit of dropping the connection, but we can't, hand on heart, state that was certainly the MSR and not the 3G network.
We've already mentioned the positioning of the MSR ports as a niggle - others include the poor build quality of the mains plug mechanism and the fact the unit only comes with a UK plug. Solwise will sell you a European plug for two quid, but you're up the spout if you want a US or Australian one, say. Bit mean, that.
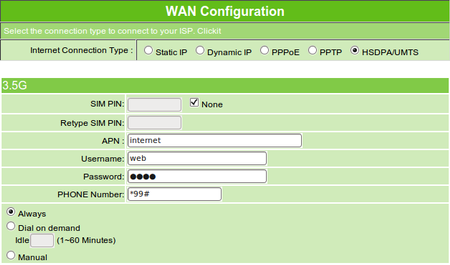
Enter your carrier's 3G dial-up details here
We also think the MSR's designer could have spaced out the USB ports a bit. You can get two standard USB plugs top to bottom, but anything thicker and you'll have to resort to extension cables.
