This article is more than 1 year old
iPhoney nano found, tested in Asia
Not the gadget you were expecting...
Review While rumours of an iPhone Nano abound, anyone knocking about China or South-East Asia with a few quid spare can buy one right now. Well, up to a point. While the 'iPhone Mini' looks and feels like a Nano-style two-thirds scale iPhone -and even comes complete with an almost-Mac icon on the back - it has absolutely sod-all to do do with the folk at Cupertino.

iPhoney and friend
The Mini - “Designed by USA. Assembled in China,” according to the case - measures up at 90 x 52 x 11mm, weighs around 70g and has a 2.5in screen of indeterminate resolution. Register Hardware's immediate impressions were that in all, it's an eminently pocketable little device and certainly feels as well made as a genuine iPhone.
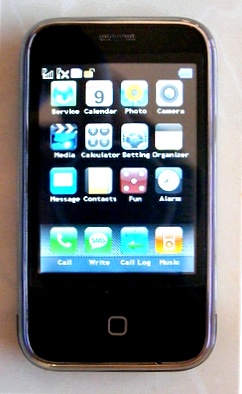
The 'iPhone' Mini: looks the part
According to the back panel, the Mini comes with 8GB of storage but we couldn't find any way of accessing it - only the supplied 1GB SD card showing up in File Explorer, so perhaps that 8GB symbol means it supports SD cards up to 8GB. Or maybe you shouldn't take that '8GB' any more seriously than the faux Apple logo.
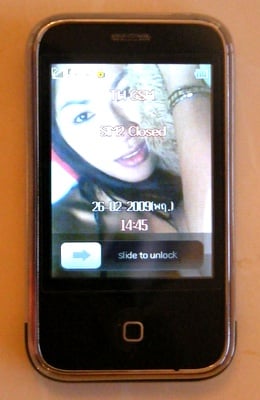
There's the lock slider...
Switch the Mini on and the usual Apple icon flashes up followed by the trademark virtual lock slider. The main menu page is also pretty much as per the iPhone, only the status bar at the top suggesting that all is not quite kosher.
When it comes to general system navigation, the Mini, while not iPhone fluid, is really no less pleasant or easy to use than the touchscreen UI on an HTC Touch or similar device. The Mini also comes with haptic feedback for those who need that extra confirmation that they've made contact.

Hang on, though - that logo's not quite right...
The Mini's touchscreen in resistive rather than capacitive, a choice no doubt partly dictated by cost and partly by the need to use a stylus to type on the diminutive virtual Qwerty keyboard which only appears in portrait mode. That's not to say you actually have to use the stylus – after some practice we managed to finger-type with around a 60 per cent chance of getting the right letter the first time.
