This article is more than 1 year old
What are the security threats?
Sophisticated Malware or just People?
"Security", as the first article in this series points out, can always be found near the top of the list of concerns of every IT manager and IT director. Unfortunately the same subject can also manage to not quite make it onto the more important list of things to do something about now.
Over the years, a diverse array of solutions has come to market, each of which claims to enhance different aspects of an organisation's IT security. Many can, indeed, enhance the capabilities in one or more areas. But security technology is only effective when deployed appropriately and, more importantly, when used correctly – by everyone in the business. And of course, security is not a one-shot operation – it cannot be assumed that the measures put in place a couple of years ago will still be appropriate today.
So this brings us to the question of what are the threats and weaknesses that must be guarded against and resolved? Several areas must be assessed. These include a direct appraisal of existing technological threats- perhaps the area most normally associated with IT security deliberations - as well as looking at how people use IT systems and the processes associated with routine business operations.
To build a reasonable picture of the threats we first need to acknowledge that the majority of corporate security breaches come about because internal staff do something that they should not or, just as likely, do not do something they should. All the same, external challenges are becoming more sophisticated as the months go by – and even ‘good’ security behaviour may not be enough to protect against all threats.
So what are the most important threats and security weaknesses that challenge business IT today? Last year, we surveyed The Register Tech Panel to find out what what they thought. Here is one finding:
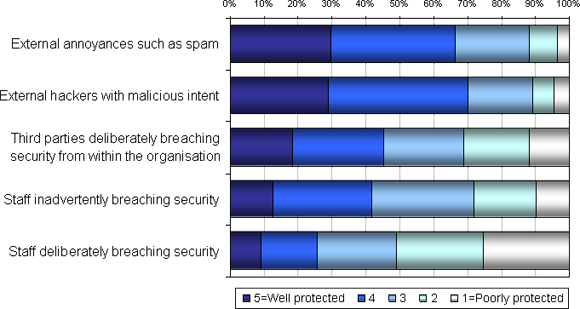
The figure above shows that even for the better-understood security challenges such as virus infections, spam, external hackers and other outside threats and annoyances, there is still a sizable community (nearly one of three) that do not consider themselves to be well protected. Issues such as anti-viral protection and systems that can scan files before they are read or executed are now a common feature of most business systems. But, as in all areas of IT, the authors of malicious code are always moving forward.
New infection vectors are being exploited, with “drive by” infections gaining particular notoriety. Here, when a user access a compromised web site, often sites of respectable entities, the web browser itself is used to insert malicious code, key loggers or Trojans onto the user’s machine. In some parts of the world this route of infection has reached similar levels as the more traditional infected email attachment. Another vector, namely infection via the use of compromised USB sticks, has become prevalent in parts Asia-Pacific.
The motives of those creating the new threats have changed dramatically over the past few years. No longer are malware authors releasing their creations just to garner notoriety or to inconvenience people. Today’s malware is more usually created with financial goals in mind as the authors, individually or in groups, try to get hold of data that can be transformed into monetary rewards. Password stealers, credit card and account number / PIN seekers are now routine targets of malware infection, with the authors of the infection either using the information themselves or selling it on for others to exploit. Identity theft should now be a major consideration for all IT systems users, at work and at home.
By the People
The figure above highlights other areas of concern for those charged with securing IT systems, and these fall very firmly into the ‘people’ space. Broadly speaking, these can be classified under the headings of ‘data leakage’ and deliberate misuse. As can be seen, a half of organisations consider themselves to be well protected against third parties breaching security from inside the firewall. Of more concern, less than a third of respondents considered their organisations to be well protected against their own staff deliberately breaching security.
These results support the often unvoiced concern that the most serious security challenges are to be found inside the enterprise, rather than outside. Data leakage, or staff inadvertently breaching security, say by losing their PC or smart phone full of encrypted data, or giving someone a USB stick loaded with sensitive data, can result in considerable financial loss and brand damage. But our survey shows that just over 40 per cent of organisations think they are reasonably well protected against this myriad of threats.
These are all real threats and the current dark economic climate, along with the increasing proportion of the world’s population getting online, is likely to exacerbate the dangers. Coupled with trends such as the rise of home working and managers looking to access corporate systems, wherever they may be, will make securing the enterprise even more demanding. An additional challenge comes from the use of new business services and technologies such as SaaS and virtualization. The need for those responsible for security to know just what equipment and users they must protect, what they do and how they work has never been clearer.
To deliver effective, secure IT services one must understand what IT assets are deployed in the company, for what they are being used and by whom.
In many organisations the quality of this knowledge is usually neither sufficient nor up to date, and in future articles we shall discussthe role of assessing existing infrastructure and developing appropriate policy. Without such an understanding, it is impossible to evaluate the nature of any potential threat, to recognise when usage patterns diverge from the expected and hence be in a position to implement appropriate security measures across the IT portfolio and indeed the organisation as a whole. ®
