This article is more than 1 year old
Banking app vuln surfaces 18 months after discovery
Patch procrastination bares 24 sites
As a security auditor for 11 years, Adriel Desautels has written his share of vulnerability advisories, but never one like the one he issued Tuesday for a software package made by a small Vermont company called Cambium Group.
In the course of penetration testing a client's website, Desautels, who is CTO of security consulting firm Netragard, says he discovered that CAMAS - the marketing name for Cambium's content management system - was riddled with vulnerabilities that made its customers' websites susceptible to breaches that could reveal administrator passwords and other sensitive data. No small deal since a significant percentage of Cambium's clients are banks, credit unions, and health care providers.
Of course, discoveries like these are a dime a dozen. What was unprecedented - at least for Desautels - was the amount of time it took to publish his findings: Almost 18 months from the time of discovery. During most of that time, he says CAMAS customers who didn't take special precautions - including Cambium Group itself, according to this Google cache - were vulnerable to attacks known as SQL injections.
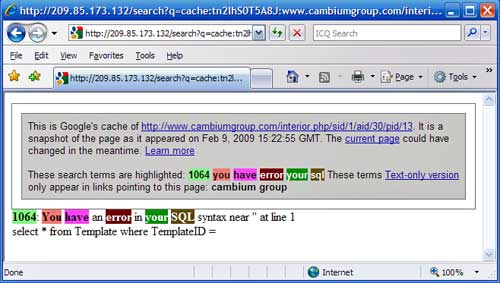
At least 23 Cambium customer websites returned SQL errors like these
"I have no doubt what so ever that the vulnerability shown in the cached link above is the exact same one that we alerted Scott Wells of in August of 2007," Desautels wrote in an email to The Register, referring to Cambium's president. "Scott Wells may have fixed the vulnerability in our customer's instance of their Cambium Group Content Management System, but he certainly did not fix the rest of his customers according to google."
The time line of the advisory shows that Cambium was notified in full detail on August 24, 2007. And yet, a review by The Register earlier this month identified 24 Cambium-driven websites that returned verbose error messages when a single additional character was added to the websites' URL. The errors were returned by the sites' SQL database and were the result of the same vulnerability, Desautels said. They began disappearing shortly after we asked Cambium Group's Wells to comment on them.
"We have addressed all but two of the sites for SQL injection vulnerabilities you listed below in your links," he wrote in a February 17 email, referring to the 24 sites identified as vulnerable. "Because our system is modular, once any type of vulnerability is found, we can update all systems very easily and quickly."
Wells also disputed claims that the errors were the same ones brought to his attention in 2007. "In regards to the Netragard claim, we immediately responded to any vulnerabilities found by Netragard in 2007," he added. "All of the recommendations that Netragard gave were followed and the site was then able to pass their validation process."
In all, Desautels's advisory lists seven website industry security categories he says CAMAS failed, including authentication, input validation, error handling, and password management.
"The Cambium Group Content Management System (CAMAS) failed most Open Web Application Security Project ('OWASP') criterion during testing," he wrote. "Netragard strongly recommends that the Cambium Group modify CAMAS to meet OWASP criterion as defined by the OWASP Testing Guide version 3."
Desautels said he walked away from the matter after it became clear he wasn't going to get the cooperation he needed to issue a public advisory. He helped his unnamed client fix the vulnerabilities, but non-disclosure agreements prevented him from publicly acknowledging the flaws, he said. Those restrictions were made moot earlier this month, when this posting to the Full-Disclosure list claimed Cambium's CMS software was vulnerable to SQL injection and other vulnerabilities.
Desautels says he's glad to finally issue the report, because he remains concerned that CAMAS customers may remain vulnerable to attack.
"The only way for the Cambium Group to properly defend against the risks that were identified by us in 2007 is to implement proper input validation, data sanitization, and well designed parameterized stored procedures," he writes. "Doing anything less is to take a short cut that might leave customers vulnerable yet still." ®
