This article is more than 1 year old
Twitter breaks Jam Festival record
You raised How Much?
Writing about Twitter is the journalistic equivalent of eating the fluff from your navel. The posh papers love it. Menopausal middle-aged hacks love it. The BBC is obsessed with it. Instead of telling us something we didn't know before, Twitter makes churnalism so easy, it practically automates the entire job.
The rest of the world, however, completely ignores it. But with the journalists' attention fixed firmly on each others' navels, they don't seem to realise what a fringe activity Twitter is. Now we can quantify this a little.
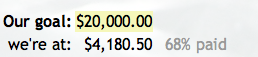
A much-trumpeted charity event called "Twestival" (from the people who brought you blooks, perhaps) received breathless coverage worth hundreds of thousands of pounds this week. 175 cities around the world took part. And it's raised just a measly $4,180 from the Twestival.fm pledge.
FAIL
Put another way, that's just 11 minutes of footballer Ashley Cole's time, and it does remind us (in more than one way) of this famous fund-raising event from 1993:
Whether it reaches the goal of $1m in a month remains to be seen. According to one Twitterer at the Guardian, Twestival is "a global charity event that has become the Live Aid of the tech world."
Um, let's hope not, since $4,000 isn't going to save many lives.
As everyone knows, Twitter is a bit of a charity-case itself: both technically and financially, it's a lost cause. That's plain to everybody, it seems, except the journalists who use it and who can't stop Twittering about Twitter.
They've formed a perfect cybernetic feedback loop, or "information cascade", to give it the current fashionable name. So while there are interesting stories to be written about the phenomenon, you're unlikely to see one from the current users ... or the BBC.
Some sort of mass intervention is probably required to save the poor hacks from this situation, but given the er, ... quality of talent there, it's probably not worth the trouble. ®
