This article is more than 1 year old
Nokia N79 smartphone
Change for change's sake?
Review We reviewed Nokia's N78 back in the summer of 2008 and even in the quick turnover world of mobile phones it almost seems a little too soon to be looking at its successor. But here it is, looking leaner, fitter and offering some significant improvements – it's almost as if Nokia just couldn't wait to get it out there.
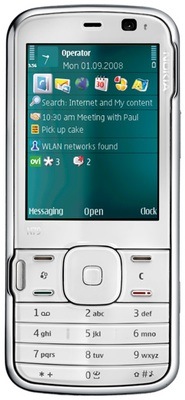
Nokia's N79: the N78, tweaked a bit
To start with the more obvious stuff, it's slightly shorter and lighter than its predecessor at 110 x 49 x 15mm and 97g - as opposed to the N78's 113 x 49 x 15mm and 102g. Estimated battery life is longer too, at 5.5 hours' talk time and 372 hours on standby - 3.2 and 320 hours, respectively, for the N78.
The trade-off is with internal memory. The N79 has 50MB, 20MB less than the N78, but it comes with a 4GB Micro SD card, though it can only handle a maximum of 8GB, which is a pity in these 16GB days. The camera now boasts five million pixels instead of three and there are two LED photo lights instead of one.
Memory aside, the N79 yields no other concessions to its predecessor and it's very well connected, with quad-band GSM, plus HSDPA 3G (3.6Mb/s), Wi-Fi, stereo-capable Bluetooth and A-GPS.
Nokia has chosen this handset to mark a return to the 'alternative covers' concept that was all the rage at the turn of the century – don't change your phone, just change the colour of the case. There are five different rear panels available in classily restrained shades of brown, green, blue, white and red, three of which are included with each phone. They're not just ordinary covers either, but "smart" XpressOn covers – they have a chip in them so that the phone's themes will automatically change to whichever colour cover you use.
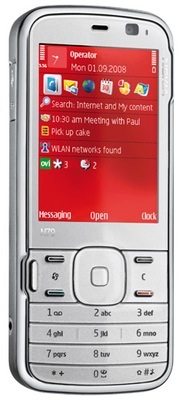
Change the colour of back cover and the screen alters too
The styling element, along with N-Gage games and photo-sharing options, give the impression that the N79 is intended to be the teen of the N series, though the price would seem to count against that. Or are teenagers getting older these days?
