This article is more than 1 year old
The benefits of co-ordinating dev and ops efforts
Yes, there are some. Really
Over the past few days here we’ve been considering the Chinese wall that can exist between development and operations teams. From a practical perspective, we know from research we ran a month or so ago that the picture ain’t quite so bad as some of the comments might suggest (Figure 1) – though it's interesting to note from the comments how bad things can get.

Well, here’s the upside. Organisations which do manage a close co-ordination between dev and ops really do reap the benefits. When we grouped the respondents to Figure 1 into 4 groups (mixing the uncoordinated responses with the small proportion that confessed working against each other, to yield a ‘Disjointed’ group), we found that those working in a collaborative manner generally were perceived as providing a better service than the others.
Indeed, looking at the two extremes, the ‘Collaborative’ group was seen as delivering IT services across the board, an order of magnitude better than their ‘Disjointed’ counterparts (Figure 2). Interestingly, the top responses equated directly to providing a higher level of service to users.
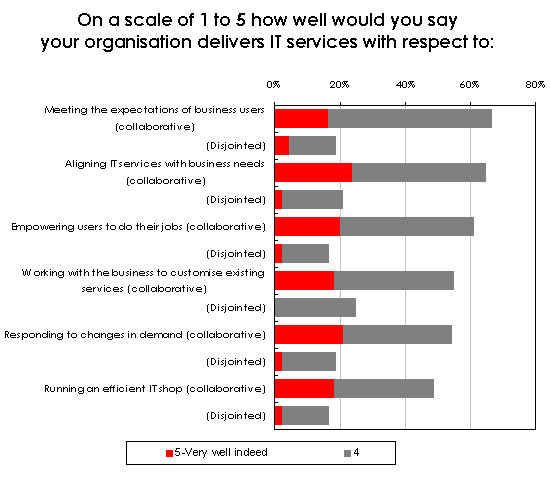
This does not make collaboration between the groups a panacea for all ills however. If we consider the main challenges, the two main issues facing most IT departments – project slippage and fire fighting – are only partially resolved for our Collaborative super-group. However, as can be seen in Figure 3, while these two points might be difficult to get right, the Disjointed group does seem to get most things wrong.
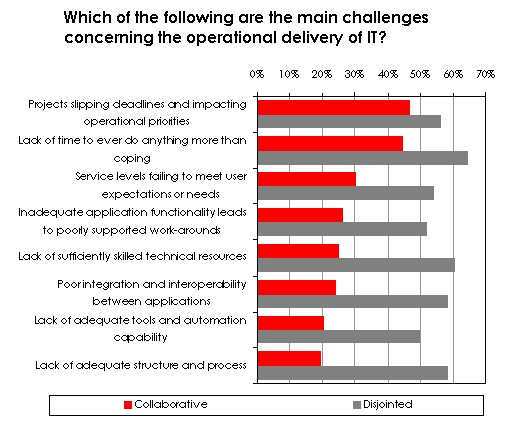
We could risk going into motherhood at this point but we won’t. The bottom line is, if you’re facing a lack of co-ordination between your development and ops teams, that’s probably the first thing to get sorted before you try to tackle anything else.
PS If you want to help us gauge the wider picture of IT-business communications, here’s a quick poll for the tea break.
