This article is more than 1 year old
The hitman, the Pirate Bay and the freetard prof
The prank that fell flat
"The Commentards are being cruel"

Unappreciated: Cramer
Cramer piled on the self-congratulation ("apart from its humorous value and cleverness, the project is interesting on many levels and layers," he boasted) - then turned to full blown self-pity, as he discovered that not everyone shared the same exalted opinion of the stunt as he did.
"What is perhaps more disturbing, however, are the openly hostile and aggressive internet user comments in blogs and on digg.com."
What an ungrateful world.
"Unlike in a comparable situation only a couple of years ago, the majority of commentators failed to see the highly parodistic and artistic nature of Pirates of the Amazon."
How could the world fail to laud the brilliance of the endeavour? Cramer had a theory.
"What the "Pirates of the Amazon" revealed," he suggested, "is that even the p2p file-sharing community is happy with its niche, and eager to keep it like that. Amazon and The Pirate Bay are two parallel systems that don't bother each other very much (although their media content is quite similar). In interfacing the two sites, the plug-in violated a taboo for Amazon.com as much for the P2P 'pirate' community which was afraid that, through the plug-in, their niche could be discovered by the mainstream and consequently shut down."
Perhaps. But there may be other explanations.
The Belfast judge described Michael Stone's claim to be staging a performance art event as "not believable". Similarly, it could be the case that as artistic pranks go, the Pirates of the Amazon simply wasn’t very good.
A good prank reveals truths which are otherwise hidden. But P2P File Sharing is hardly a secret. It dominates the media, "mainstream" or otherwise, and the practice is widespread.
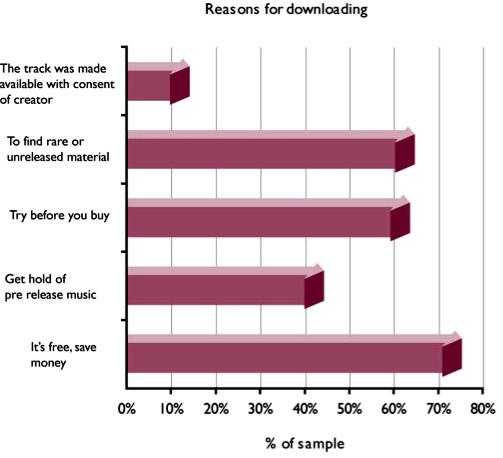
63 per cent of British internet users download unlicensed music - and the average amount downloaded is 53 tracks per months. People are refreshingly honest about why they download - it saves paying money for music - and surprisingly keen to become legitimate, paying for a decent P2P service.
A good prank doesn't preach to the converted, either.
Lousy comedians blame their audience for being stupid; lousy politicians blame the voters. But Cramer can't countenance the possibility that his work was not striking, original or subversive. He has to conclude that the audience secretly shares Cramer's high opinion of his students work, but it won't say so.
Faced with a prank that revealed no new power structures at all, and didn't tell anyone anything they didn't already know, Cramer resorts to "inventing" a truth hitherto unrevealed.
So Cramer's reaction ranges from persecution, via self-pity, to self-deception. (Persecution myths are rife amongst the anti-creator crowd, I've discovered. Perhaps these are required to sustain the Freetards' sense of moral superiority?)
Since Duchamp's urinal, a great deal of modern art has been a "prank" against the art establishment. Maybe that's why now, state-funded "pranks" like the Pirates plug-in - designed to preach to the converted - feel so stale. Or it could be Cramer's own deeply conservative (and misanthropic) outlook. By design, the course ensures his students fulfill a narrow set of ideological obligations - all of which are de rigeur in modern media theory.
And that, we must conclude, is exactly what the modern state requires from its "radicals". Rather than being outside the tent pissing in, they're quite content to be on the inside, launching Firefox browser plug-ins outwards. Repressive regimes once persecuted dissidents - now they merely need give them cushy jobs on Media Theory courses to render them useless. They'll do the rest.
And such is the fate of state-funded art - prank or otherwise. ®
Andrew warmly welcomes your comments.