This article is more than 1 year old
Still sending naked email? Get your protection here
Buckle your seatbelt, encrypt your bits
Step 3: Install the Enigmail add-on for Thunderbird
If you plan to receive encrypted emails on a regular basis, you'll probably want a seamless way to decrypt them. Plenty of email clients, Thunderbird among them, have ways to do just that. This tutorial assumes you've already installed Thunderbird. If you haven't, you can either install it first or skip this step and find some other way to decrypt your messages.
Navigate to this page on the add-ons section of the Mozilla website. Click on the "Download now" link and save the file (at time of writing it was enigmail-0.95.7-tb+sm.xpi) to your desktop.
In Thunderbird, go to Tools > Add-ons and then click the Install button at the bottom left of the popup window. In the "Select an extension to install" window, change the folder to your desktop. In the list of files, highlight the Enigmail file you just downloaded and choose Open. In the resulting Software Installation window, click Install Now. Then restart Thunderbird.
Enigmail should immediately open an OpenPGP Setup Wizard that prompts you to select a key to sign and encrypt email. Highlight the key you just created and select Next.
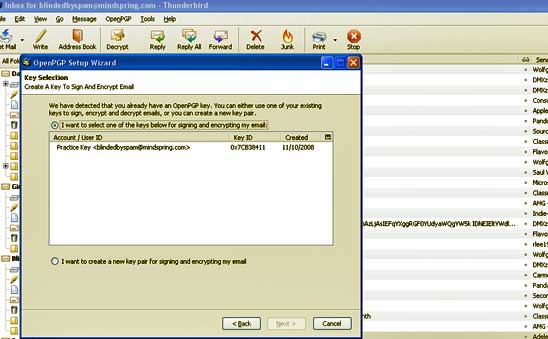
Once Enigmail opens, choose the key you just created
By now, one of the contacts you emailed earlier should have had time to send you an encrypted message using your public key. When you use Thunderbird to open it, you'll be prompted for your passphrase. Enter the passphrase you chose when you generated your key pair. If all goes well, Enigmail will decrypt the message and it will look something like this:
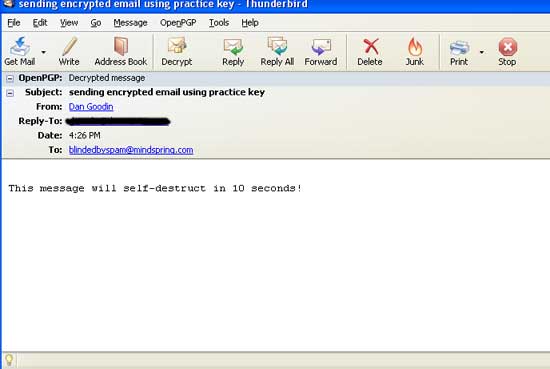
With the private key, email looks like this
Congratulations. You've just decrypted your first email. For an idea what the same message looks like to anyone without the key, open the same email on a web-based email service or a client that hasn't been set up to work with your key pair. It will look something like this:
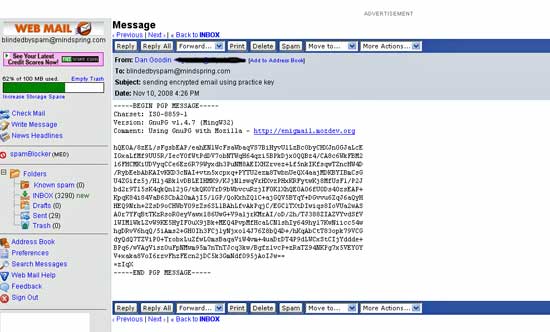
To a snoop without the private key, the same email looks like this
Note that subject lines are never encrypted, so remember to never include private information there.
