This article is more than 1 year old
Police vet live music, DJs for 'terror risk'
Locking down garage...and RnB, basement
A dozen London boroughs have implemented a "risk assessment" policy for live music that permits the police to ban any live music if they fail to receive personal details from the performers 14 days in advance. The demand explicitly singles out performances and musical styles favoured by the black community: garage and R&B, and MCs and DJs.
However all musical performances - from one man playing a guitar on up - are subject to the demands once implemented by the council. And the threat is serious: failure to comply "may jeopardise future events by the promoter or the venue".
UK Music chief Feargal Sharkey told a House of Commons select committee that the policy had already been used to pull the plug on an afternoon charity concert of school bands in a public park organised by a local councillor.
"No alcohol would be sold, tickets were limited to three maximum, and the councillor offered to supply eight registered doormen. Police objected on the grounds that the names, addresses and dates of birth of the young performer could not be provided," said Sharkey, speaking to the Department of Culture Media and Sport's hearing on venue licensing today.
"Live music is now a threat to the prevention of terrorism", he concluded.
In response, Detective Superintendent Dave Eyles from the Met's clubs and vice office told us that 10,000 such Risk Assessments would be processed this year. He said they weren't compulsory:
"We can't demand it - we recommend that you provide it as best practice. But you're bloody silly if you don't, because you're putting your venue at risk."
The Risk Assessment, or to give its official name "Form 696" can be found here (Word doc 184kb or Google HTML cache). We've highlighted a couple of excerpts below.
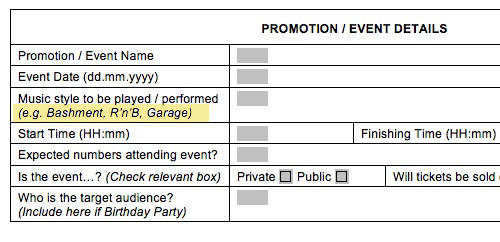
Bashment Jaxx? Black urban musical styles are singled out
Licensing of live music is nominally under the democratic control of local authorities. However, few councillors dare contradict the advice of the constabulary - even when such advice exceeds the police's authority, as it does here.
John Whittingdale, the Culture select committee chairman, described it as "a consequence of the Metropolitan Poice exceeding what is required by law".

The police want information 14 days in advance to assess the risk of a terror threat
'Propensity to violence'
"Have a look at the papers and tell me where the black-on-black shootings happen? They're around the night time economy," said Eyles.
"Music promotions attract people who have a propensity to use violence. That's not speculation. We have a duty to prevent that from happening."
But even if that's true, why vet then the performers? Unless the performers attack the audience, Sid Vicious-style in the fictional Great Rock and Roll Swindle?
"We're not vetting the performers - we're looking at the audience. It's not the music it's the people who follow it, who use that event as a catalyst to commit crimes.
But, Form 696 explictly vets the performers. We read it out.
"Some venues use their inhouse DJs all the time - others fly them in from around the world. It's not just their track record in the UK we're looking at but we're looking worldwide - what has happened historically at those events".
With the police groaning under bureaucracy, was 10,000 extra forms really justified?
"We can effectively look at those venues and say by putting in some measures as a last resort, canceling the event, we can prevent crime."
But didn't Sharkey's example - a kids concert in the park - suggest that the system was being abused?
"I would doubt that's factually correct," said Eyles. "I've never known an event to be cancelled because a Risk Assessment wasn't completed. If we went to the organisers and asked them to pull it, we would be laughed out of court. I cannot believe that would happen. In itself, it's not grounds to shut an event down."
Readers can browse 696 and judge for themselves. ®
