This article is more than 1 year old
Link spammers set up shop on GMTV sofa website
Breakfast station briefly pwned after domain name snafu
The website of breakfast TV station GMTV was colonised by spammers over the weekend after its domain lapsed.
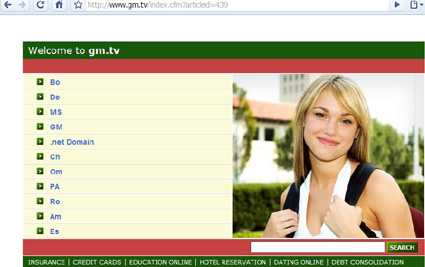
Enough to make you choke on your cornflakes
Instead of offering information on presenters or topics to be covered on the show the site became a showcase for links to dating and debt consolidation websites. GMTV - best known for its brightly coloured sofa-filled set and bland interviews conducted with celebrities by Lorraine Kelly - became a link farm for spammers after its domain came up for grabs.
Reg readers were quick to tell us about the problem, which initially appeared to be a simple web defacement. Normality returned after GMTV's webmaster flashed the plastic and renewed the web site's registration. The site has since been restored to full health.
Security watchers at Sophos did not register any spam as a result of the ruse, which was quickly nipped in the bud. The GMTV website was infected by the BadSrc-C strain of malware on 10 August, Sophos said, but that seems unrelated to its more recent problems.
GMTV's techies acknowledge our request for comment but said that the person who handled the issue was tied up. We have heard nothing more back at time of writing.
GMTV has held the breakfast TV franchise for the main commercial channel (ITV1) in the UK since 1993. An estimated 5 million Brits tune in every morning to watch the magazine-style soft news program made up of interviews, chat, news bulletins and quizzes. The station was fined £2m last year by regulators after it emerged that the winners of some competitions were selected before phone lines closed, leaving thousands of punters shelling out to enter competitions they had no chance of winning. ®
