This article is more than 1 year old
Apple MacBook
A complete overhaul only improves this neat notebook
A point to note, though: the cheaper of the two new MacBooks lacks the keyboard backlight. Did it really add to much to the machine's bill of materials, Apple?
The standard pair of USB 2.0 ports are still there on the left-hand edge of the unit, along with digital audio inputs and outputs, and a "SuperDrive" multi-format CD/DVD burner. However, Apple’s traditional Firewire port has disappeared. That’s not surprising – the writing has been on the wall for Firewire for some time, although it’s very disappointing for those of us that use Firewire hard disks, or have camcorders with Firewire connectors.
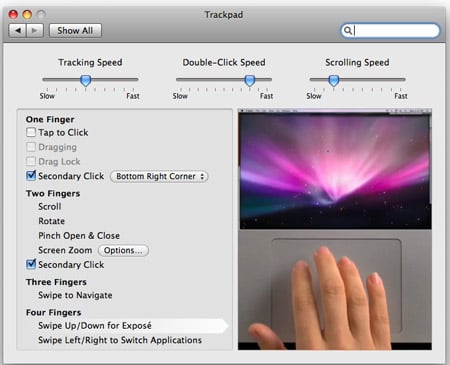
The new trackpad allows the use of multi-finger ‘gestures’
Gone too is the mini DVI monitor port. In its place, there’s a new mini DisplayPort interface for hooking up an external monitor – such as the new 24in monitor that Apple has designed specifically for use with its laptops. The DisplayPort upgrade makes sense - it's the emerging standard for digital computer-monitor connections, but the full-size port isn't exactly large, leaving us wonder whether this is really just another excuse to force folk to buy an adaptor. Certainly, you don't get one in the box.
Again, the new MacBook Pro had the new mini DisplayPort connector, so it’s clear that the two product lines really are starting to merge together now. That’s good news for buyers who might want to hook the laptop up to a larger monitor, perhaps to use the MacBook as their main desktop machine, as it means that they can now get the features they need without having to pay for the more expensive MacBook Pro.
In fact, Apple CEO Steve Jobs – with his fabled ‘reality distortion field’ obviously set to 11 – actually implied that this was a price cut as the MacBook now provides features and performance comparable to that of the MacBook Pro for less than £1000.

The Air influences are clear in the keyboard
There’s a kind of logic to this, as the new MacBook really does blur the once-clear dividing line between Apple’s ‘pro’ and ‘consumer’ laptops. And, to be fair, the price of the new MacBook still compares quite favourably to rival premium-name brands.
