This article is more than 1 year old
Win a Palm Treo Pro smartphone
One £399 handset could be yours
Competition To celebrate the launch of its latest Windows Mobile smartphone, Palm wants to give one of the gadgets away to one lucky Register Hardware reader.
Palm has commandeered London's Truman Brewery in Brick Lane for the whole of next week as a showcase for the new handset. With food from Michelin starred chef Brett Graham, the event features nightly celebrity hosts from the worlds of business, sport, music, comedy and the media - including Piers Morgan, Karren Brady and The Human League.
The Black Sheep Pub event takes place from 13-17 October. To register for free tickets to this exclusive gig, pop over to http://www.blacksheeppub.net.
But first, just answer the following questions and click the Enter button to see if you could be dialing in with your very own Palm Treo Pro.
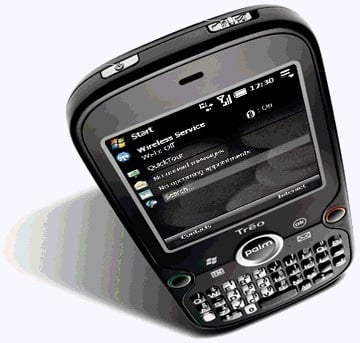
The Treo Pro packs in everything you'd expect from a modern smartphone: stylish shiny black design, HSDPA 3G connectivity, 802.11b/g Wi-Fi, Bluetooth 2.0 and on-board GPS. The skinny handset boasts the traditional Palm Qwerty micro keyboard, which makes entering email and tapping out texts a doddle.
This competition is now closed
Rules and Ts&Cs
The Register Hardware Palm Treo Pro Competition is open to all Register Hardware readers in the UK aged 18 or above. No purchase is necessary. The Palm Treo Pro handset will be offered SIM-free and without airtime. Only one entry per reader will be accepted. Multiple entries will be disqualified. All entries must be submitted with a valid email address. The winner will be the first name drawn from entrants who have correctly answered the questions posed. The winner will be notified by email with 28 days of the closing date. The winner must confirm his or her postal address promptly to claim the prize. The prize is subject to availability, and Register Hardware reserves the right to substitute an alternative prize of similar nature and/or the same value should this become necessary due to circumstances beyond our control. Register Hardware will not be liable if the prize does not reach the winner for reasons beyond our control, or if the prize is damaged during delivery. The decision of the Editor is final, and no correspondence will be entered into. The competition is not open to employees of Situation Publishing or Palm, their agents or their families.
