This article is more than 1 year old
Jesus Phone vuln delivers fanboys to phishermen
Apple silent on 'pretty dumb design flaw'
A security expert is advising iPhone users to steer clear of the device's default email application until engineers rework what he calls "a pretty dumb design flaw" that could expose users' email addresses to spammers and other online frauds.
The warning comes two and months after researcher Aviv Raff first reported two email-related vulnerabilities in the iPhone to Apple's security department. Apple has updated the gadget three times since then, but has yet to fix either weakness. Late last week, after Apple refused to say when the patches might be delivered, Raff decided to publicly disclose the technical details.
The first defect resides in Apple's Mail application. Unlike most email clients, the program automatically downloads images embedded in HTML mail messages. That can be a problem for people who want to fly under the radar of spammers because the downloading of so-called beacon images embedded in spam and phishing messages are one technique scammers use to sort live email accounts from inactive ones.
"The iPhone's Mail application downloads all images automatically, and there is NO WAY to disable this feature!" Raff writes in this blog item. "So, my only suggestion is to avoid using the Mail application until a fix is available."
Raff disclosed details of a separate iPhone flaw that puts users at risk of visiting websites secretly under the control of miscreants. The flaw, which resides in Mail and the iPhone version of the Safari browser, truncates the names of long internet addresses, making it them appear to be friendly when in fact they are not.
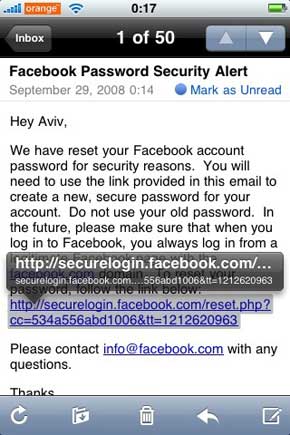
In the screenshot above, for example, the link appears to point to https://securelogin.facebook.com/reset.php?cc=534a556abd1006&tt=1212620963 when in fact, it points to a site controlled by Raff. When a user clicks on the link, Safari opens and the address bar shows only https://securelogin.facebook.com/reset.php?cc=534a556abd1006&tt=1212620963, further making it hard for users to know they've been led astray.
"The problem here is that an attacker can set a long subdomain (~24 characters) that, when cut off in the middle, will look as if it's a trusted domain," Raff wrote.
Apple representatives didn't respond to an email requesting comment for this story. ®
