This article is more than 1 year old
Reg readers: Distributed software development is hard
But is there hope?
This leads to the question of which parts of the development process are safe to distribute out to satellite or outsourced teams without running into trouble. The general consensus is to keep the critical early part of the life cycle (specification, analysis and design) in-house along with overall project management, putting the focus of remote activity on coding, testing and, to a lesser degree, integration work. (Figure 5)
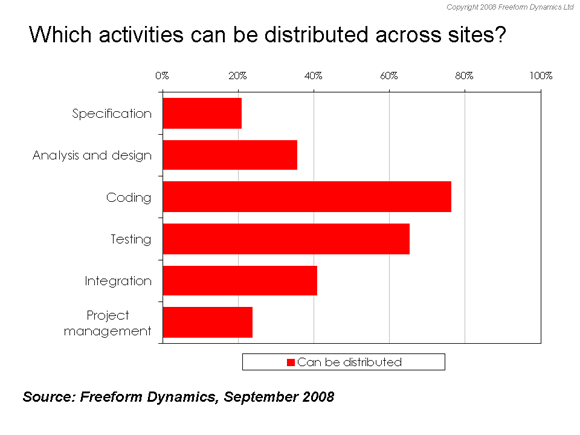
Figure 5
Looking a bit more closely at this, we can get some insight into why the peer-to-peer model is attractive to some, despite the associated challenges our poll suggests. With a more even distribution of skill sets and experience between teams, those taking the peer-to-peer approach are more comfortable distributing some of the critical up-front specification, analysis and design, as well as integration and overall project management (Figure 6).
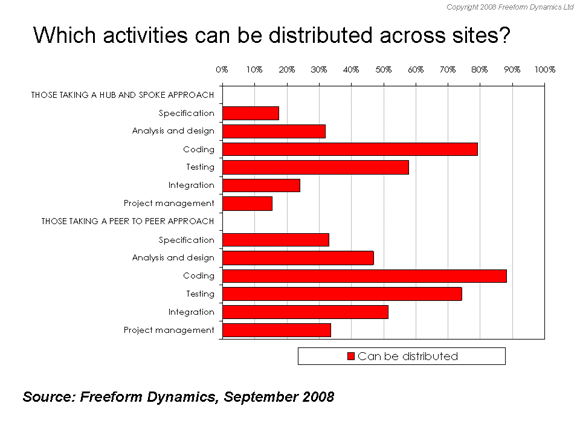
Figure 6
Going down the peer to peer route can therefore equate to better overall flexibility from a resourcing perspective, which in turn will have benefits in terms of overall delivery and responsiveness to the business. It’s not the only option or indeed the easiest, but it certainly merits consideration.
