This article is more than 1 year old
Securing the world against terrorists, scammers, and thugs
A day in the life of a cyber gumshoe
An information technology employee for one of the world's top stock brokerages is let go, but before he leaves, he plants a logic bomb that knocks 3,000 of the firm's workstations offline.
The internal network of a federal agency is penetrated by a drug cartel and used to obscure international communications among various members.
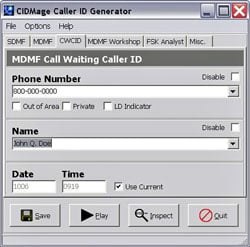
A law firm discovers that an impostor has been using a caller ID generator to call members of the public and pose as one of its attorneys.
These are some of the emergencies today's cyber investigators are expected to respond to, the head of forensics for Chevron told attendees of a security conference Wednesday. Given the ongoing spike in computer-based crime, and new laws requiring firms to store ever more amounts of digital data, the workload will only increase.
"This is a field that is in its infancy," Robert Schperberg, forensics lead for Chevron, said at the MIS Training Institute's IT Security World conference in San Francisco. "In today's environment, it's more needed than ever, especially in the states - if you've heard of the new rules of federal civil procedures."
The rules mandate how businesses must store, gather and safeguard information that's admitted into evidence in federal cases.
Rather than focus on such banal parts of the job, however, Schperberg talked about the ongoing fight he and his counterparts engage in to keep their networks free of scammers, organized crime gangs and even terrorists.
A case in point is public branch exchange, or PBX, telephone networks used by many organizations to route phone calls. A hacked mailbox may seem of minimal consequence until you consider the practice some groups use to avoid paying hefty fees for international calls. The crooks change the outgoing message to someone saying "Hello?," pausing for 10 seconds, and saying "yes." That's often enough to fool a long-distance operator into believing someone has just consented to being charged for a third-party call.
"Nothing is checked but at the end of the month, you get a whopper of a bill," he said.
Hacks into phone networks can carry much higher stakes, as was the case during the the March 11, 2004 train bombings in Madrid, when terrorists allegedly tried to activate the explosives using mobile phone-based detonators. Rather than calling the mobile phone themselves, the terrorists routed the calls through a series of PBX systems owned by unnamed companies, he said.
In some cases, the detective work required can be meticulous - and expensive. When the aforementioned logic bomb knocked 3,000 work stations offline at a brokerage, at IT administrator who was recently dismissed became the prime suspect. After getting a search warrant and confiscating his hard drive, investigators were forced to scour through its remains using an electron microscope, and the price of $100,000 per pass.
Schperberg, who previously did forensics work for the Sheriff's Department in Alameda County, California, also showed off plenty of toys during his presentation, which was titled "A Day in the Life of a Cyber-Crime Fighter."
One was a CIDmage caller ID generator (a screenshot is to your right), which scammers frequently use to impersonate others. He also showed off a highly portable disk cloner that's perfect for covert investigations. "The Cloner," as he referred to it, included a console with a fully functional keyboard that allows disk images to be time-stamped with information that's needed for the contents to be admitted into evidence. ®
