This article is more than 1 year old
Ad hoc malware police besiege net neutrality
When does crime fighting become censorship?
Piercing the Online Rat's Nest
Of course, the difference between the online and physical worlds is stark when it comes to law and order, and that has a lot to do with the current state of affairs. In most industrialized societies, there are a variety of authorities that crime victims can call on, and assuming a reasonably high priority has been assigned to enforcing laws against the offense, there's a reasonable likelihood that the perpetrators will be caught - or at least deterred from victimizing others.
On the internet, a rat's nest of jurisdictional and technical complications provide shelter for a huge proportion of the crime taking place. Someone in Chicago or London who gets duped into installing malware has virtually no chance of catching the responsible miscreant, who is frequently on a different continent. Even worse, there is little authorities in either the US or the UK can do to take down the offending website. This inability has given online criminals a sense of impunity.
To see just how skilled miscreants have gotten at milking the system, witness the shell game that took place late last week on Intercage's network. When we contacted Patrick Jordan, senior malware researcher at security provider Sunbelt Software, he had no trouble producing an Intercage IP address (69.50.190.135/?to=010388&from=ru, to be exact) being used to send visitors to a potpourri of abusive sites. The first time we visited it we were led to scan.antispyware-free-scanner.com, which falsely claimed our PC was infected and needed to be cleaned using software that would be provided free of charge. (Note, we used a virtual machine to visit all suspicious addresses. We strongly recommend steering clear of these sites unless you know what you're doing.)
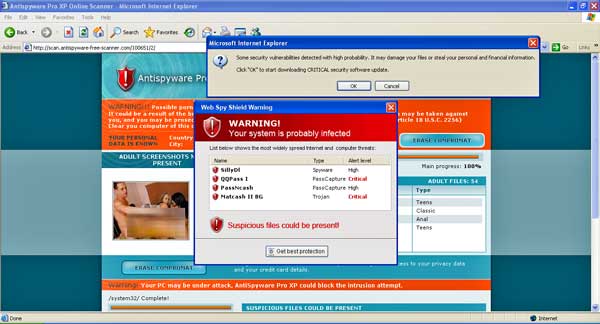
This site was brought to you by Intercage
The next time we hit the Intercage IP we were directed to hardcore-free-video.com, a site claiming we needed to install a free codec before viewing content. Those who take the bait find that their domain name system server will be changed to one that sends them to fraudulent pages.
On Wednesday, we brought this IP address to the attention of Intercage president and owner Emil Kacperski, who shut it down within a half hour. But within hours, Jordan discovered the miscreants simply moved their rotational scam site to 69.50.190.136/?to=010388&from=ru, just one address higher in Intercage's IP range. Shell games like this one are a never-ending fixture on Intercage that has gone on for years, a chorus of security experts say. They have become convinced the only way to put an end to it is for providers of Intercage to pull the plug on their customer.
"What [Intercage] did, no matter their vehement denials otherwise, was assist in the process of dramatically hurting a lot of people, whether it was because of somebody having to shell out a lot of money to buy a security product or because they were extorted," says Alex Eckelberry, Sunbelt's president. "Rogue ISPs who have been friendly to bad guys should be on notice that their activities are being watched and are being publicly reported and there may be a price to pay."
Malware Main Conduit
Indeed, the cost to Intercage has been abundant. Host.net, a backbone provider that serves Intercage, decided to dump its customer following several reports. One came from Spamhaus and another, issued two weeks ago by an organization called HostExploit.com, portrayed Intercage as "a main conduit for financial scams, identity theft, spam and malware."
"Obviously, there's a lot of pressure to do something about this," says Randy Epstein, co-founder of Host.net. "Our acceptable use policy allows us to disconnect customers that are violating our rules. You have a right to protect your company."
Indeed, companies should be able to police their own networks. We've argued as much for more than a year. The question is whether take-downs should be summarily executed within a few days of a report being issued or taken only as a matter of last resort.
According to Kacperski, none of the security researchers publicly criticizing Intercage have ever bothered to call or email him or otherwise report the abusive sites using the company's resources.
"If these abuse people are serious about stopping malware sites, you would think they would at least send me a list of sites to quickly remove," he says. "How hard is to send an email and say, 'Emil, these are the sites that I'm seeing. Can you please knock them off. They're causing damage.'"
We asked a handful of Intercage's most vocal critics if they sent take down requests to Kacperski. None said yes. "In his defense, what may have finally happened is that malware researchers stopped bothering to report" abusive sites," Eckelberry says.
Kacperski says his company swiftly responds to messages sent to abuseatintercage.com, and in the two instances we reported fraudulent sites, the company removed them in less than an hour. Yes, it's possible those reports got special treatment since they included the IP address of a known security reporter, but because few others seem to send abuse dispatches, there's no way of knowing for sure.
