This article is more than 1 year old
Acer Aspire One A110
The Eee-beater to beat
By way of a test, we ran a basic Gimp filter test by applying the Gaussian blur filter to a 25.3mb 2048 x 1366 pixel JPEG image, a process that took an average of 7.2s. This compared well the results of the same test performed on the Atom powered Asus EeePC 901 which managed 10.85s when the CPU's set to the standard 1.6GHz setting.
Gimp Results
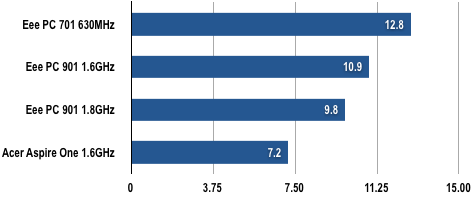
Time in seconds
Shorter bars are better
Wireless communication is limited to 802.11b/g Wi-Fi so no Bluetooth and no 3G, though the SIM slot lurking behind the battery is a sure indication that the latter will be coming to the AA1 in due course. In the meantime, accessing the net over a cellular network will involve getting up close and personal with a USB modem and the relevant drivers. That's easy with the XP version, less so with Linux.
A feature currently unique to the AA1 is the seamless storage expansion. Shoving a £20 Class 2 8GB SDHC into secone memory card slot we mentioned before resulted in the system telling us we now had 11GB of storage from a potential maximum of 14GB, up from 3.4GB out of 6.4GB. In case you're wondering where the missing storage is, it's the One's 1GB Swap partition.