This article is more than 1 year old
Were the snatched Brit sailors in 'disputed waters'?
Renewed Iran matelot-napping brouhaha dissected
Analysis Last week, the Times obtained an MoD document relating to the Iran sailors seizure fracas last year. It was heavily redacted, but there was a paragraph left which referred to the well-known fact that part of the maritime boundary between Iraqi and Iranian waters has never been agreed by Iran.
The Times ran this under the headline "Report reveals Iran seized British sailors in disputed waters". This was widely picked up by other media, who went further - for instance the Guardian, under the headline "Bordering on Deceit" with a strap: "Last year we were told that British naval officers were indisputably in Iraqi waters. If only we had been more sceptical".
Actually, a lot of people were at the time, pointing out that the last time Iran agreed to a border with Iraq was in 1975 - and that border ran only to the mouth of the Shatt al-Arab waterway which divides the two countries. How, these people asked, could there be an agreed border out at sea when the Iranians had never signed up to one? How, in other words, could the UK Ministry of Defence be so positive that its people hadn't infringed on Iranian territory?
The MoD didn't help itself much on this, issuing a heavily simplifed map:
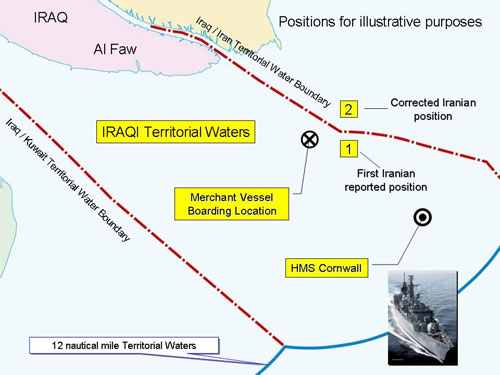
MoD's map of events.
This, which shows the coastline in ordinary landlubber map style at the high-water mark, has a Territorial Waters (TTW) line clearly drawn on. But, as the Times' MoD document said:
The last agreed demarcation (1975 Algiers Accord) delineated TTW along the Shatt al Arab only. At no juncture have TTW been settled beyond the mouth of this river.
For anyone who'd like to read the released document in all its redacted glory, be our guest (Word doc): we thought we'd get a copy of our own and read the whole thing before mouthing off.
So - bang to rights. The MoD (and Defence Minister Des Browne) was lying. There was and is no territorial line beyond the river mouth.
But hold on. On the Reg defence desk we're always up for a bit of MoD bashing, but in this case Her Majesty's officers and mandarins are only really guilty of failing to explain themselves properly.
