This article is more than 1 year old
'Diamondville' to shine as Intel's next Atom
Inside the 'Silverthorne' architecture
IDF Having launched the first batch of 45nm Atom-brand processors yesterday, Intel today began touting the next set, these ones aimed at sub-laptops and small form-factor desktops rather than Mobile Internet Devices (MIDs).

Codename watchers will be wondering where 'Diamondville' fits into Intel's Atom family, and now we know for sure. It's the part that will become the Atom N series, leaving the Atom Z series - aka 'Silverthorne' - for MIDs.
Diamondville and Silverthorne are based on the same microarchitecture, developed from the ground up under the Silverthorne codename since that was the first chip of the family to be developed. Both versions are fully compatible with the 'Merom' Core 2 Duo, so they're limited to SSE 3 rather than SSE 4, part of the 'Penryn' Core 2s.
Small, isn't it?
But where Silverthorne lacks support for 64-bit addressing and Virtualisation Technology - they're not really needed on a handheld - they may well be present in Diamondville CPUs, almost certainly in the case of the desktop-oriented models.
Expect a number of mobile Diamondvilles, but the one Intel touted today is the N270. The chip giant confirmed it will be clocked at 1.6GHz and that it'll be paired with Intel's 945GSE northbridge and ICH7M southbridge rather than the more expensive, MID-oriented SCH series that combine with the Atom Zs to form Centrino Atom, a brand that's unlikely to be applied to Atom-based sub-notebooks.
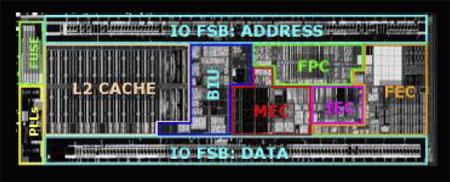
Inside Silverthorne
Desktop-centric Diamondvilles will be accompanied by the 945GC northbridge and ICH7 southbridge. Power consumption is less important here than it is with laptops, so expect Intel to drive these as-yet-publicly-unnamed Atoms on cost above all else.
The first desktop Diamondville is expected to be the 1.6GHz 230, though Intel itself has yet to confirm these numbers. Given it has the same clock speed as the N270, we might suggest it'll actually ship with a higher model number.
