This article is more than 1 year old
Jules Verne gets intimate with ISS
Successful approach to within 11 metres
The European Space Agency's "Jules Verne" Automated Transfer Vehicle yesterday manoevered itself to within 11 metres of the docking port of the ISS's Russian Zvezda module during a second "demonstration day" designed to test its "critical optical navigation system" prior to a scheduled docking on 3 April.
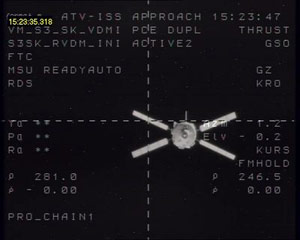 The space truck, captured here at 246.5 metres from the ISS by the ESA's Docking Video System, successfully deployed its Videometer technology to autonomously approach the ISS.
The space truck, captured here at 246.5 metres from the ISS by the ESA's Docking Video System, successfully deployed its Videometer technology to autonomously approach the ISS.
Once the ATV was in its closest approach, ISS astronauts issued a "Retreat command" which sent Jules Verne back to a 19 metre point, followed by an "Escape command", which "automatically took Jules Verne to a safe location away from the ISS".*
Astrium ATV Project Manager Nicolas Chamussy enthused: "This demonstration day confirmes the performance of the vehicle is even better than we had hoped for. This is a world premier for automated rendezvous using optical sensors, following the world’s first demonstration of relative GPS navigation between Jules Verne and the Station performed on Saturday."
ESA’s ATV Project Manager John Ellwood joined the party with: "I’m known for my understatements, but the only word that comes to mind about today is impressive. It was impressive to see how Jules Verne, the staff at the ATV Control Centre, the control centres in Moscow and Houston pulled together today. It was a perfect dress-rehearsal for Thursday."
The ESA used the approach to "inspect some thermal blankets on the exterior of the spacecraft that had become degraded", but doesn't anticipate these will affect Jules Verne's docking with the ISS, starting at 16:41 CEST (14:41 GMT) on Thursday. ®
Bootnote
*While the Jules Verne is designed to operate autonomously, ISS crew have a number of override options available "if there is a serious problem during rendezvous". The ESA explains: "The crew can interrupt the ATV approach in four different ways: HOLD, RETREAT, ESCAPE or ABORT. The action to be taken depends on the type of anomaly.
"The main action to be taken by the crew in case of failures occurring at distances further away than 20 metres is to report to mission controllers. The space vehicle is sufficiently far away for the ground controllers - having access to all data and not just a limited selection, to take the best decision.
"At distances closer than 20 metres, the crew will send the ATV away using the ESCAPE mode if the ATV moves outside the approach monitoring corridor or in case of malfunctions of the safety system. ABORT has the same effect as ESCAPE but uses independent software and hardware. It is used as a last resort should the main ATV computers or piloting hardware fail completely."
