This article is more than 1 year old
Rebit: This is your grandmother's data backup
Simplicity has a price
Time Machine for OSX has got the Apple platform's fuss-less data backup covered quite nicely. But where can a technical nincompoop turn for brainless Windows backup?
There's still room for third party companies to jump into the backup droolbucket here. And that's where Rebit backup shows up.
 Rebit is certainly not the cheapest backup solution out there. It also lacks many of the features alternative external hard drive packages offer. What you're paying for is the simplicity. It's PC and laptop backup for people only recently upgrading from the abacus — the Aunt Lucy or freshly unthawed Encino Man in your life.
Rebit is certainly not the cheapest backup solution out there. It also lacks many of the features alternative external hard drive packages offer. What you're paying for is the simplicity. It's PC and laptop backup for people only recently upgrading from the abacus — the Aunt Lucy or freshly unthawed Encino Man in your life.
Reg readers may want to steer clear of Rebit for their own personal use. But that's not to say it doesn't have its place in the backup market. You might have a loved one that would appreciate the completely hands-off approach to data protection.
But we could always try some sympathetic magic. Smash your head against the desk. Harder. HARDER! Repeat the process for approximately five minutes.
Now baby needs to buy you a Rebit.
The units come in 80GB, 120GB, 160GB, 320GB, and 500GB sizes. Obviously, you'll need one that's equal or larger than the computer's hard hard drive. Prices range from $169 to $270. The drives are designed for typically configured Windows boxes with one disk drive. Keep in mind Rebit units do not work as a storage device. It's for backup, and backup only.
Once you're plugged in, you're prompted to start protecting the computer. You'll also be given the ubiquitous terms of service contract (that you know you really should read, but never do).
And that's pretty much it.
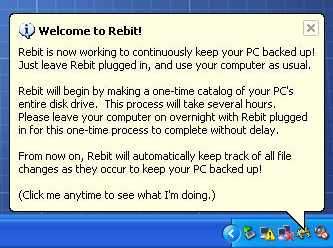
Rebit will start to do its thing, which can take a while. The software recommends leaving the computer on overnight with the unit plugged in. During this process, Rebit backs up the system partition (in most cases the C drive). This is also the only time Rebit will back up any other partitions on the disk. After that, it's only giving the system partition the lovin'.
Once the initial process is over and done with Rebit keeps a continuous watch on the drive. Any new files created or old files that are changed get a backup copy. When you delete a file on the PC, the backup copy or copies remain in the Rebit.
Past files are kept on Rebit until the unit becomes full. When the capacity limit is reached, the oldest backup is deleted to make room for a newer, current backup. Recovery consists of going into the Rebit and dragging and dropping the archived file where you want it.
If the entire disk bites it, there's a Rebit Recovery CD that can restore the system to a new drive. However, the unit cannot be used for cross-computer migration. Operating system files are backed up on the Rebit, so the old system files may cock up a new PC righteously.
And there you have it. The Rebit is a question of weighing its limitations against a person's desire to have as little to do with data backup as humanly possible.
Units are available through various channel partners in the US and Europe and online at www.rebit.com. ®
