This article is more than 1 year old
Geeks fight the smelter with embedded processor-based box
The Climate Computer
Looking past even a laptop chip, they're studying how to make a very powerful machine around customized embedded processors.
This so-called Climate Computer could run on myriad multi-core 650MHz chips and consume just a fraction of power compared to, say, an Opteron-based cluster or an IBM BlueGene machine, according to Simon.
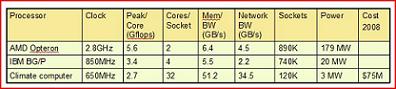
The Climate Computer
"We can get the same computer power at one-twentieth of the power consumption," Simon said.
You can catch a proposed layout for a Climate Computer here.
Simon sees this type of experiment as being necessary for a world in which computer centers will consume between 20MW and 130MW. (All of Berkeley's labs today consume 20MW total.)
The researchers look to work on this project "for about a year so and then go to the Department of Energy and say, 'We are ready to the build the real prototype.'"
The highest-end computer users will balk at any performance trade offs, but a many-cored system with such low power consumption may prove attractive in three to four years to a large set of less demanding customers, especially when you consider complementary trends.
All of the major chip makers will continue to release processors with more and more cores, forcing software makers to craft better multi-threaded code. Around these general purpose chips we're seeing a rise of accelerators from the graphics and FPGA realms, which also require improved coding techniques.
With tens and hundreds of cores floating about on each chip and accelerators, the processor almost becomes a modern day version of what the transistor was 30 to 40 years ago, Simon noted. As hardware and software vendors embrace this notion, even systems running on very low power chips stand to demonstrate remarkable performance at cranking through software threads.
Large service providers like Google and Microsoft will likely continue with their current plans.
"But that is not the wave of the future," Simon said. "(Those systems) will remain for the big players, but the mainstream will switch directions in the decade."
Utility computing bigots might argue that average customers will tap into centralized systems before something like a solid embedded processor-based machine makes it to market. Such criticism, however, relies on an awful lot of prognostication.
It's refreshing to find computer scientists returning to the extreme low-power idea as these larger shifts in computing take place because the Green Destiny concept once exhibited a great deal of potential.®
Bootnote
The presentation about the Climate Simulator pilot project can be found here in PDF. A detailed article in the International Journal of High Performance Computing Applications can be found here in PDF as well. A lot of the original work has been done by John Shalf, Lenny Oliker, and Michael Wehner, the three authors of this paper.
