Robustness analysis in practice: take the test
As with our previous extracts, it's time for a quiz. This time, there's no top-10 list, but - instead - a visual puzzle. The robustness diagram excerpt (shown next) highlights a number of errors, including at least one in the use case text, in the last sentence of the basic course, and two where the text and the diagram don't match up. Have fun finding them all.
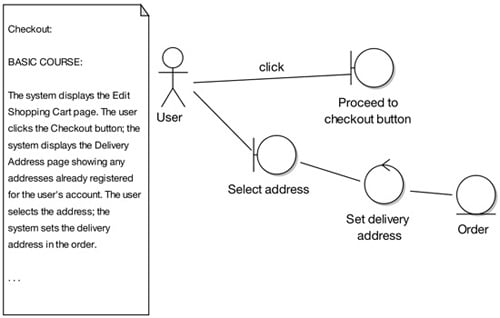
Spot the error - what's wrong with this diagram?
Did you spot the problems? Overall, the diagram doesn't match the description. Digging deeper, the first mistake is that the text starts at an earlier point in time than the diagram (a common mistake). An easy way to spot this type of error is to use the highlighter test.
The second error - the GUI widget is shown as a boundary object - is another common mistake. A GUI widget such as a button is too fine grained to be the boundary object; instead, the boundary object should be the screen or web page.
The third is fundamental: an entire chunk of the use-case text has been left off the diagram. It's surprising how often this happens. It's usually a sign that somebody isn't working through the use case one sentence at a time.
Our fourth and final problem is a direct consequence of ambiguous use case text. The text wasn't tied closely enough to the objects, so the modeler just sort of went off in a pseudo-random direction and, lacking the real boundary object to work with, used "Select address" as the boundary object, even though it's a verb and, therefore, is a controller masquerading as a boundary object. And as we're sure you know by now, actors can't talk directly to controllers.
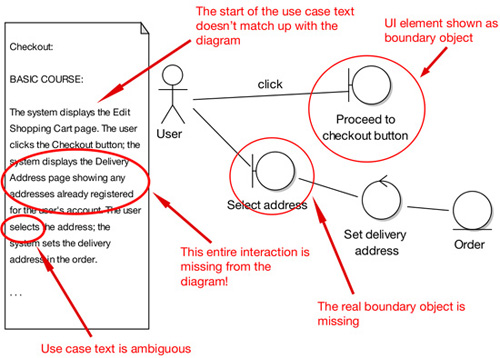
Seeing red - mistakes highlighted
In redrawing the diagram, shown next, we discovered another ambiguity in the text - funny how that happens!
The text "the system displays the Delivery Address page showing any addresses already registered for the user's account" implies some search and retrieval initialization behavior, which currently also doesn't appear anywhere on the diagram.
