This article is more than 1 year old
Robo Development Conference in pictures
Know thy roboenemy
Robo Developer Robots. Sure, they're evil, but are they a threat to us yet?
The Register takes a look at the show floor of Robo Developer Conference in San Jose to see how the coming war with machines may play out.
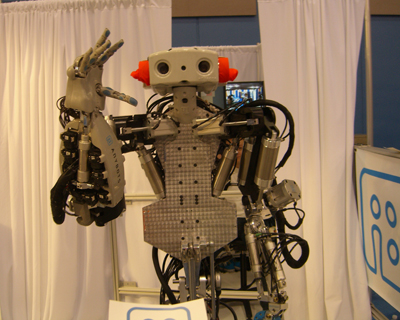
Our first stop is a robot named Monty, from Anybots. He stands at about 5'7" and has one fully articulated hand, driven by 18 motors and one gripper. Monty is remotely controlled by a man behind a curtain, who is wearing various sensors that let Monty mimic his movements. According to Anybots, Monty can perform a wide range of manual labor tasks. For instance, his publicity shot shows Monty washing dishes — which I would assume is a fantastic way to electrocute yourself and loved ones.
And would you trust a filthy robot with The Heirloom China?
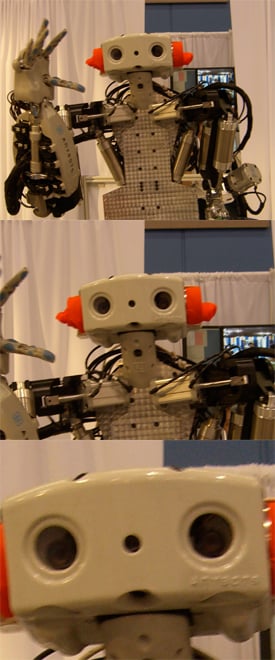
Would you?
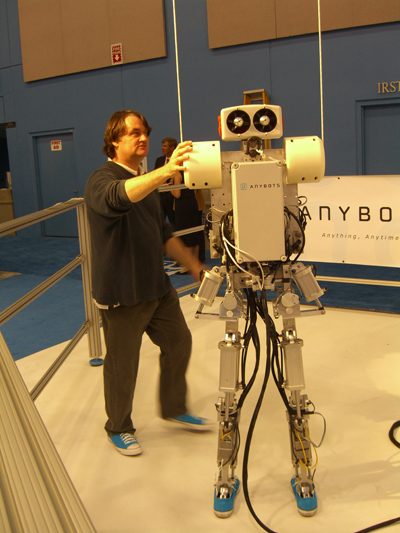
Anybots also has a walking automaton named Dexter. This robot quickly showed its true sinister nature by repeatedly spasming violently before it pitched headfirst into the crowd. Those bungee cords are not for show.
I was told by several vendors that getting a robot to walk is one of the hardest things to do. This doesn't come as a surprise. The constant chatter on the show floor was regularly accented by the dull "thump" of robots hitting the floor. Take any robot demonstration — what so often is just beyond the frame of sight is two engineers, poised nervously at the sidelines like ball retrievers at a tennis tournament.
