This article is more than 1 year old
Binary interfaces in component development
A template class with static data - how can that possibly go wrong?
In the next example (see Figure 2) the code is logically and textually identical apart from the usual dllimport and dllexport specifiers. Later in this article we’ll see more about these and how they work, but for this example they’re not important. Instead, we want to focus on the behaviour change; our singleton is no longer living up to its name. Two singleton objects are created and the Gang of Four are already drafting a blog entry, complaining about our corruption of their pattern.
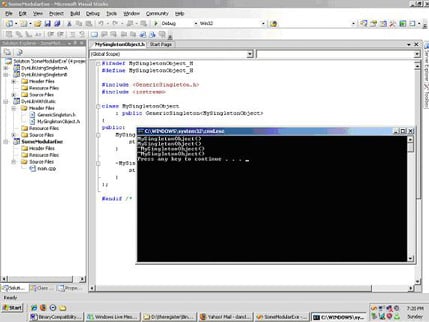
So what has happened here? Earlier we noted that a C++ compiler would (with few exceptions) instantiate a class template and its member functions when it’s specialised and the template definitions for the member functions are available. The Windows behaviour is that both A and B are dlls, making calls to member functions in our singleton class. The template definitions are in the header file and hence always available (they are always instantiated). As a result, both A.dll and B.dll contain a definition for our static variable. However, if we try to confirm this by using the dumpbin command that comes with Visual Studio, there’s no trace of our static variable anywhere in the dynamic libraries (see Figure 3). In the linker map output (see Figure 4), we can see that the symbols are still in the library but the identifying names have been eliminated.
Figure 3: Dumpbin of all dll information
(N.B. no mention of our static variable!).
D:\ …\code\somemodularexe\Release>dumpbin /all DynLibUsingSingletonA.dll
SECTION HEADER #1
.text name
119ED virtual size
1000 virtual address (10001000 to 100129EC)
12000 size of raw data
1000 file pointer to raw data (00001000 to 00012FFF)
0 file pointer to relocation table
0 file pointer to line numbers
0 number of relocations
0 number of line numbers
60000020 flags
Code
Execute Read
RAW DATA #1
10001000: C7 01 B4 31 01 10 E9 17 2D 00 00 CC CC CC CC CC Ç.´1..é.-..ÌÌÌÌÌ
10001010: 56 8B F1 C7 06 B4 31 01 10 E8 04 2D 00 00 F6 44 V.ñÇ.´1..è.-..öD
10001020: 24 08 01 74 09 56 E8 D9 2D 00 00 83 C4 04 8B C6 $..t.VèÙ-...Ä..Æ
10001030: 5E C2 04 00 CC CC CC CC CC CC CC CC CC CC CC CC ^Â..ÌÌÌÌÌÌÌÌÌÌÌÌ
10001040: 8B 44 24 10 8B 4C 24 0C 8B 54 24 08 56 8B 74 24 .D$..L$..T$.V.t$
… …. …
Figure 4: Linker map output showing variable definition. 0004:00001b60 ?myNsExportedVar@A@@3HA 100b2b60 A.obj 0004:00001b64 ?m_instance@?$GenericSingleton@VMySingletonObject@@@@0VMySingletonObject@@A
The reason we can’t see the static objects in the dumpbin report is that in our example we haven’t tagged the instantiated objects of static duration as dllexport. As a result, in Microsoft’s portable executable format, the linker doesn’t add them to either the export section of the dll - or even preserve the symbol names. After all, if a symbol isn’t exported there’s no need to put its name into the dll; as all references to it are known at link time. However, under such a system we cannot expect our static data at runtime to behave as C++ indicates that they should, with a single instance across the program.
