This article is more than 1 year old
ID thieves bring ease of use to trafficking forums
Stolen info translated into German, Albanian and French at no additional cost
As cyber crime goes mainstream, a working knowledge of English is no longer a required skill for identity thieves trafficking in stolen credit card numbers and other personal data. Just ask Matthew Miller, a pharmacist from Pennsylvania, who recently learned miscreants had translated some of his personal details into French before blasting them out to a discussion group frequented by online con artists.
"I feel violated about that, quite frankly," Miller said shortly after seeing a screenshot that listed his "nom," "prenom" and other personal information translated so it could be consumed by those without a working understanding of English. "Anything that I have with my personal history would be accessible to these people."
Miller's case is hardly an isolated example.
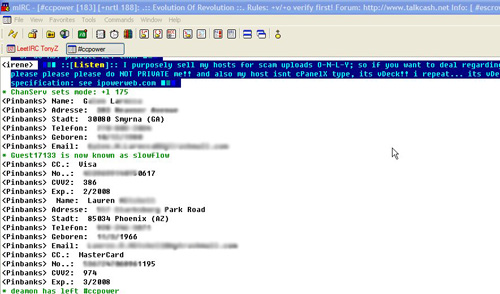
The above screenshot is part of a trend that started about nine months ago in which purloined information is translated into languages including French, German and Albanian to make it more appealing to would-be buyers. As soon as a victim is tricked into entering the details on a phishing site, a CGI script converts the fields when compiling a database.
In addition to name, address, date of birth and credit card and CVV2 numbers, many of the entries also include the victim's social security number and mother's maiden name, as was the case with Miller.
"Right now, it seems like everybody in the world knows my social security number," Miller said.
He said he fell "hook, line and sinker" for an eBay phishing scam about 12 months ago and was in the process of rehabilitating his identity when his personal information was misappropriated again in May.
With so many of traffickers speaking a native language other than English, it's only natural that databases would provide better ease of use, according to Dan Clements, president of CardCops, a division of the Affinion Group that monitors online forums for stolen credit card information. Being located in places far out of reach of most US-based law enforcement agencies means they aren't likely to be stopped anytime soon.
"They're on foreign soil, and their drilling down on America and they have the ability to drill down on America indefinitely," Clements said. ®
