This article is more than 1 year old
M2M jumps beyond the line
The wireless Heineken effect?
Mobile Workshop Much debate about the use of wireless technology in business tends to revolve around providing mobile and remote workers with access to central systems of one kind or another.
The growing popularity of notebook data cards and handheld email devices among professionals is probably the most obvious illustration of this, though recent Freeform Dynamics research tells us that around 50 per cent of organisations with sizeable field service operations are deploying handhelds to engineers, technicians, and so on.
Wireless and mobile technology is therefore becoming integral to the way many businesses are operating, providing a whole range of benefits arising from simply allowing the mobile workforce to participate electronically and directly in business processes in the same way as their office and depot dwelling colleagues.
There is, however, another area in which wireless appears to be having an impact. This is in the so-called Machine to Machine communication space (M2M), or referred to by the equivalent term "Wireless Telemetry". As the jargon suggests, the idea here is to make use of wireless technology to allow machines to communicate directly with other machines, without a human being in the loop.
The idea of M2M is in itself nothing new and has been utilised, for example, to allow more efficient monitoring and control of assets in locations that are difficult, dangerous, or expensive to reach, such as equipment installed on oil rigs, pipelines, railway networks, and so on.
The emphasis has traditionally been on wired communications, though this has the obvious disadvantage and constraint that a cable must be run to the equipment in question. In many circumstances this can be expensive, even if less so than sending a person along to physically check things. There are also safety implications associated with running electrical cables through hazardous areas, and maintenance considerations when connecting through hostile environments in which cables may be easily damaged.
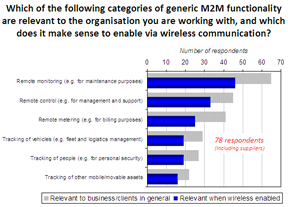
This is where wireless M2M comes into play. While not always applicable in every environment, feedback gathered from 78 organisations with an interest in M2M - both solution providers (x23) and end user organisations (x55) - suggests there is a definite trend towards the use of wireless in this whole area:
As the findings show, while wired M2M communications are still dominant, as we would expect, wireless is considered relevant in approximately two-thirds of cases within pretty much all important M2M categories.