This article is more than 1 year old
In the beginning, there was the flowchart...
Software diagramming - a warning from history
Stob
Those who can, do. Those who can't, make those who can draw a picture
My first effort in instructing computers, about 30 years ago, was drawing a flowchart. Here it is as I remember it, albeit without the smears and crossings-out with which my 14-year-old self doubtless decorated the original.
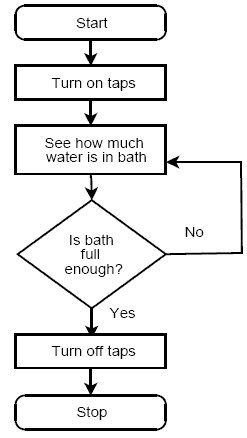 We were unconstrained, in those far off days, by such piffling issues as web interface, unit tests, or code efficiency. Nor did we have to contend, as did some of my luckier contemporaries, with complex systems where punched cards were sent off to a local bureau.
We were unconstrained, in those far off days, by such piffling issues as web interface, unit tests, or code efficiency. Nor did we have to contend, as did some of my luckier contemporaries, with complex systems where punched cards were sent off to a local bureau.
The fact was we simply had no hardware at all, unless you counted the clear plastic stencil that had to be bought from WH Smith's. The only opportunity we got to exercise our "code" was by slogging through a "dry run", a notably unsatisfactory exercise involving an imaginary computer. It was, to borrow a crisp, vulgar phrase from Robert Robinson, "...like losing one's virginity without having the f*ck".
When a school micro finally did arrive, a year or two later, those of us who had been bitten by the programming bug gleefully threw our inky stencils aside and proved we could tackle non-Radox problems without diagramatic props.
But after that uninspiring formative experience, I have tended to be suspicious of those who would oblige me to make pretty pictures when I should be banging out code. This article is a record of how those suspicions have panned out.
Again with the flowchart
Flowchart worship persisted long beyond the point where even British management might have been expected to spot they were rubbish. In the mid-1980s, I watched from a safe distance as a colleague attempted to code up an entire application from a flowchart specification. This massive document, beautifully hand-Rotringed on best engineering paper, was hundreds of pages long. Its pages all looked something like this:
Only much bigger and scarier. Any sense of structure of the original program had, naturally, been entirely suppressed.
My colleague operated a dual coping strategy to deal with this monster: during working hours she wept delicately and persistently; during the lunch break she scanned the job ads. I don't believe the port was ever completed.
During the late 1980s, the flowchart was at last jeered out of software development. A host of alternatives competed to occupy its throne, usually proprietary and usually associated with an expensive CASE tool. Although some approaches really hit the spot - for example relational database schema design - a lot of other diagramming techniques just left you with the sensation of being lectured at.
For example, there was something called the context data flow diagram. The version I was taught comprised a single circle, surrounded by labelled arrows. A hypothetical clearing bank system would look like this:
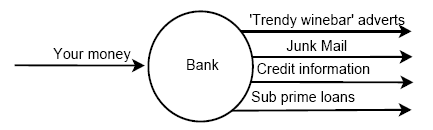
Other not-terribly-good diagrams I was obliged to draw at around the same time were structure charts (I think these were just function call hierarchies); thread diagrams (dull short stories expressed as data flows) and, a little later, class hierarchies.
These last I believe were a hangover from Smalltalk, and when first introduced (always as an IDE feature called a "class browser") were thought to be a vital prerequisite to any OO development. It took a while before it was noticed that nobody used them. This realisation may have coincided with Borland releasing a version of its C++ framework called "OWL". Previous class libraries had displayed as elegant inverted "V" shapes. But this particular version of OWL, the first to make extensive use of multiple inheritance, looked like a basket of wool that had been romped in by an exceptionally lively litter of kittens.
It was enough to put you off your templates.
