This article is more than 1 year old
EVGA 680i LT SLI nForce-based motherboard
Cut-down 680i - or shoved up 650i?
Review For some time, Nvidia's 600 family of chipsets has had a gaping chasm between the nForce 650i SLI, which typically sells for £90, and the nForce 680i SLI, which starts at £165. Enter the 680i LT SLI chipset, a budget version of the 680i SLI.
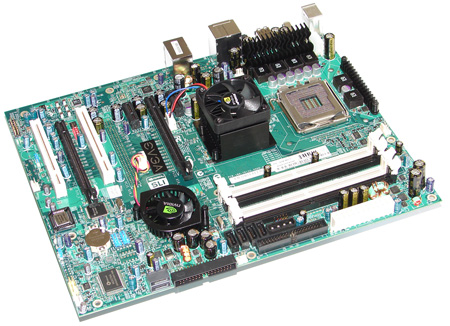
EVGA's nForce 680i LT SLI board from the front
As the name suggests, the nForce 650i SLI supports dual Nvidia graphics cards for gaming, but SLI is just about the only significant feature and even then it's the half-hearted sort with 16 PCI Express lanes assigned to the two slots.
The nForce 680i SLI has a whole host of extra features, including SLI with 16 PCIe lanes for each graphics card, plus a third graphics slot with eight PCIe lanes, which will be handy come the day games can use a third graphics card to handle physics.
The 680i increases the number of available SATA hard drive links from four ports to six, and adds support for a 1333MHz frontside bus. The number of USB ports on the I/O panel climbs from four to six and there's a second Gigabit Ethernet connection. On the board you'll likely find power and reset micro buttons along with an LED readout to display POST codes. The final addition is support for SLI memory, which can run up to 1200MHz. Not only is this maximum supported memory speed incredibly fast, but the memory can be automatically overclocked by Nvidia's nTune utility.
That's a long list of features, but it comes at a very high price, so it didn't come as a huge surprise when Nvidia launched the nForce 680i LT SLI as a lower cost alternative.
Unfortunately, we made a couple of slips of the keyboard in our news coverage so it's time to put the record straight with a comparative review using two EVGA motherboards. One is the nForce 680i SLI with revision A2 of the chipset and the other is the nForce 680i LT SLI. These rather unimaginative chipset-labels-as-EVGA-model-names are quite appropriate as these motherboards seem to follow the Nvidia reference design very closely.
