This article is more than 1 year old
Security meltdown at Hotel Chocolat
Website displays personal details
Contrary to popular belief, it seems that chocolate isn't always simply a pleasurable oral substitute for sex.
In fact, chocolate munchers are a rowdy bunch - a bloke in the midlands who is rather partial to a "Rocky Road Slab" is also "fantastic in bed", apparently...
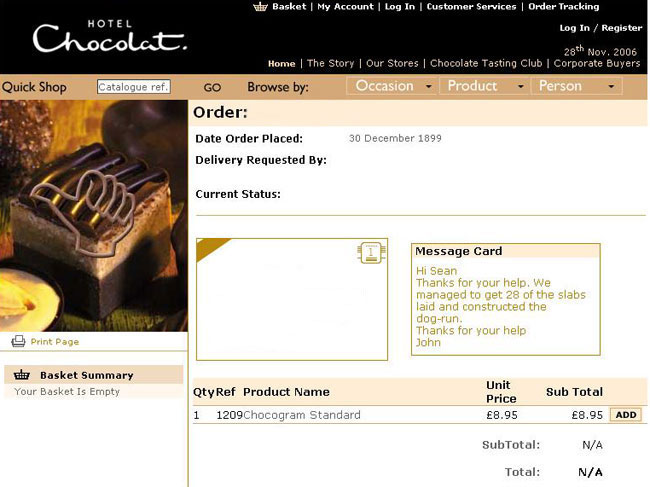
How do we know this? One El Reg reader alerted us to the fact that online choccy provider Hotel Chocolat had been inadvertently displaying personal information on its website.
Names, addresses, and orders could be seen alongside intimate messages left for the intended recipient of chocolatey goodness.
Although the website was not displaying anything as private as credit card details, the fact that names and addresses were viewable is enough to violate data protection.
As soon as she became aware of the privacy issue she emailed Hotel Chocolat and politely suggested it fixed what was clearly a security flaw.
However, it took several emails before the website responded, which meant personal details were displayed for at least a day - though likely for longer than this - before the issue was rectified.
The website has a privacy page that states the following:
"Security is a priority at Hotel Chocolat...You need to know that a website is legitimate, and transactions are secure before you buy. To address these issues, the Hotel Chocolat website uses a Digital Certificate from BT TrustWise."
Hotel Chocolat also uses Verisign, which should encrypt information before it is sent across the web to help secure the site from hackers/wrong-doers/people in dark bedrooms with nothing better to do, etc.
But for at least 24 hours the website offered dubious types the opportunity to print off personal information.
By mid-afternoon yesterday the website had finally been fixed, it seems, thanks largely to our reader's determination.
Meanwhile, Hotel Chocolat isn't talking to us despite several phonecalls. Seems they're, er, fully booked or something. ®
