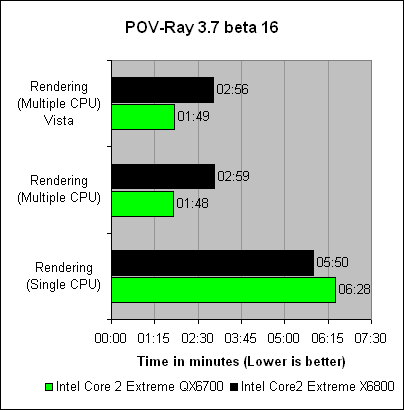
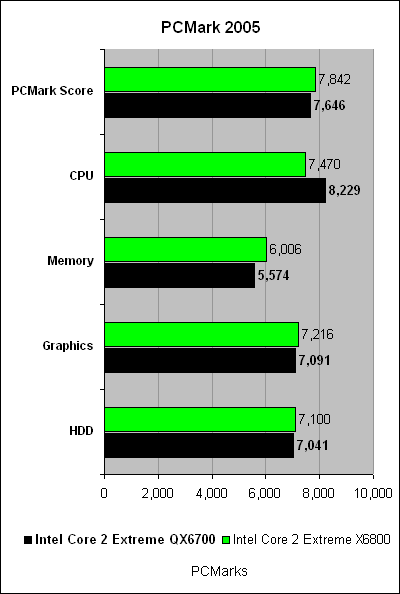
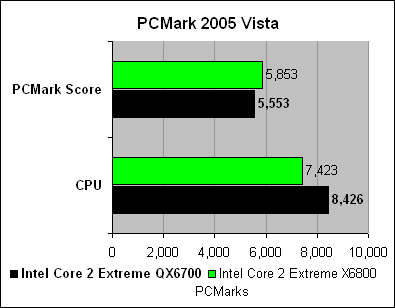
This article is more than 1 year old
Other stories you might like
Meta lets Llama 3 LLM out to graze, claims it can give Google and Anthropic a kicking
Plans multilingual 400 billion parameter version, but starts with more modest fare
AI + ML19 Apr 2024 | 3
US Air Force says AI-controlled F-16 fighter jet has been dogfighting with humans
Video Robo-plane was made to restrain itself so as not to harm pilot or airframe
AI + ML18 Apr 2024 | 4
Ransomware feared as IT 'issues' force Octapharma Plasma to close 150+ centers
Source blames BlackSuit infection – as separately ISP Frontier confirms cyberattack
Cyber-crime18 Apr 2024 | 2
A different view from the edge
How Dell NativeEdge provides the single pane of glass which harmonizes your IT and OT perspective
Sponsored Feature
Crooks exploit OpenMetadata holes to mine crypto – and leave a sob story for victims
'I want to buy a car. That's all'
Cyber-crime18 Apr 2024 |
Stability AI decimates staff just weeks after CEO's exit
More like Instability AI, right kids?
AI + ML18 Apr 2024 | 4
IBM accused of cheating its own executive assistants out of overtime pay
Big Blue bosses retaliate against those seeking overtime, lawsuit claims
On-Prem18 Apr 2024 | 5
Google fires 28 staff after sit-in protest against Israeli cloud deal ends in arrests
Alphabet Workers Union says bosses refuse to listen to concerns
Off-Prem18 Apr 2024 | 18
Feds hit coding boot camp with big fine for allegedly conning students
Do not pass go, do not collect $200, says government agency
Software18 Apr 2024 |
Microsoft aims to triple datacenter capacity to fuel AI boom
And it's far from the only hyperscaler getting in on the act
On-Prem18 Apr 2024 | 1
House passes bill banning Uncle Sam from snooping on citizens via data brokers
Vote met strong opposition from Biden's office
Security18 Apr 2024 | 13
October 2025 will be a support massacre for a bunch of Microsoft products
Not just Windows 10. Don't forget about Exchange Server, Skype for Business, and all those Office installations
Software18 Apr 2024 | 18